SHCTF2024
本文最后更新于 2024年11月13日 上午
总排第28名,后续会对web复现
week1
Misc
签到题
公众号发对应内容就可以得到flag
Rasterizing Traffic
给的流量包,wireshark导出全部内容,中间的三个flag拼接是假的
最后一个导入010得到一个图片,网上搜索了一番知道是光栅隐写吧(是这么叫嘛)直接上exp,会跑出五个图片,拼接一下就行
1 | |
拜师之旅①
给的图片不能正常查看,用010查看给加上正常的png开头给到图片,发现没有flag,crc爆破一下宽高得到flag

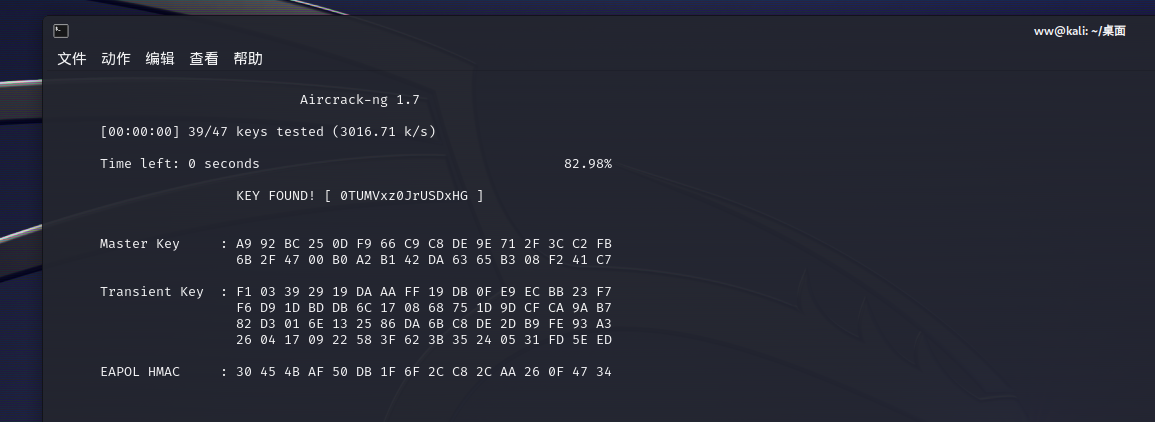
有WiFi干嘛不用呢?
简单的学一下
csv里面给了BSSID: EE:52:37:27:75:EB
may里面应该是密码字典,写个脚本提取一下内容,然后kali进行运行
aircrack-ng 01.cap -w pass.txt -b EE:52:37:27:75:EB -e target
1 | |
真真假假?遮遮掩掩!
第一层我直接用伪加密工具Zipcenop进行的然后到了第二层,给了hint,SHCTF??????FTCHS,有点眼熟可以进行简单的猜测,最后得出是202410,然后带入解压得到flag,在线掩码爆破也行
Crypto
EzAES
1 | |
Hello Crypto
1 | |
baby_mod
参考了一下某比赛的wp,需要用到LLL算法,在本地微调之后的脚本如下,不太懂密码,本地的sagemath也不太灵光
1 | |
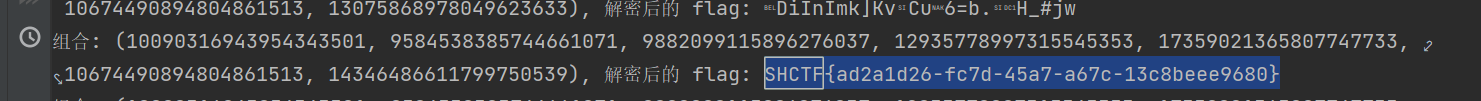
factor
首先用yafu对N进行分解,然后带入对十选七进行全排列不重复,最后在答案区搜索SHCTF得到flag
1 | |
Pwn
签个到吧
1 | |
No stack overflow1
checksec一下发现有nx保护
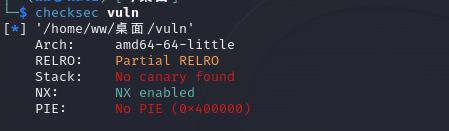
ida打开发现有backdoor里面写入了bin/sh
一个gets的栈溢出,前面加\x00可以绕过,上exp
1 | |
No stack overflow2
checksec一下开了nx
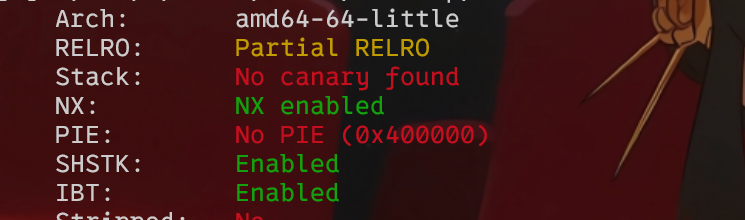
用ida打开,F5查看伪代码,先看main函数,有大小比较用-1绕过,没有system和sh,溢出点在read函数
用ROP gadget –binary ‘vuln’ –only ‘pop|ret’ ,查找rdi和ret的地址
1 | |
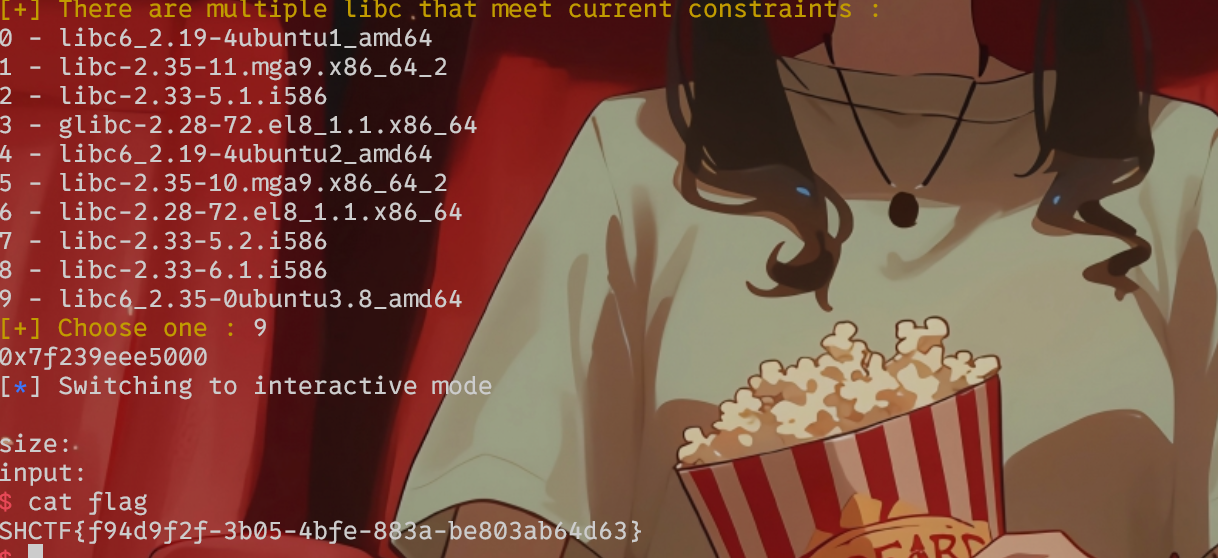
Web
1zflask
先看/robots.txt,再看/s3recttt下载了文件,看一下在/api下面可以执行,进行传参得到flag
1 | |
ez_gittt
githack坏了,用gitdump下来,然后如下操作
蛐蛐?蛐蛐!
看源码有提示根据提示前往,然后构造payload
1 | |
1 | |
jvav
还没学过java,问gpt跑一下
1 | |
poppopop
1 | |
单身十八年的手速
直接js定位到alert然后base64解密得到flag
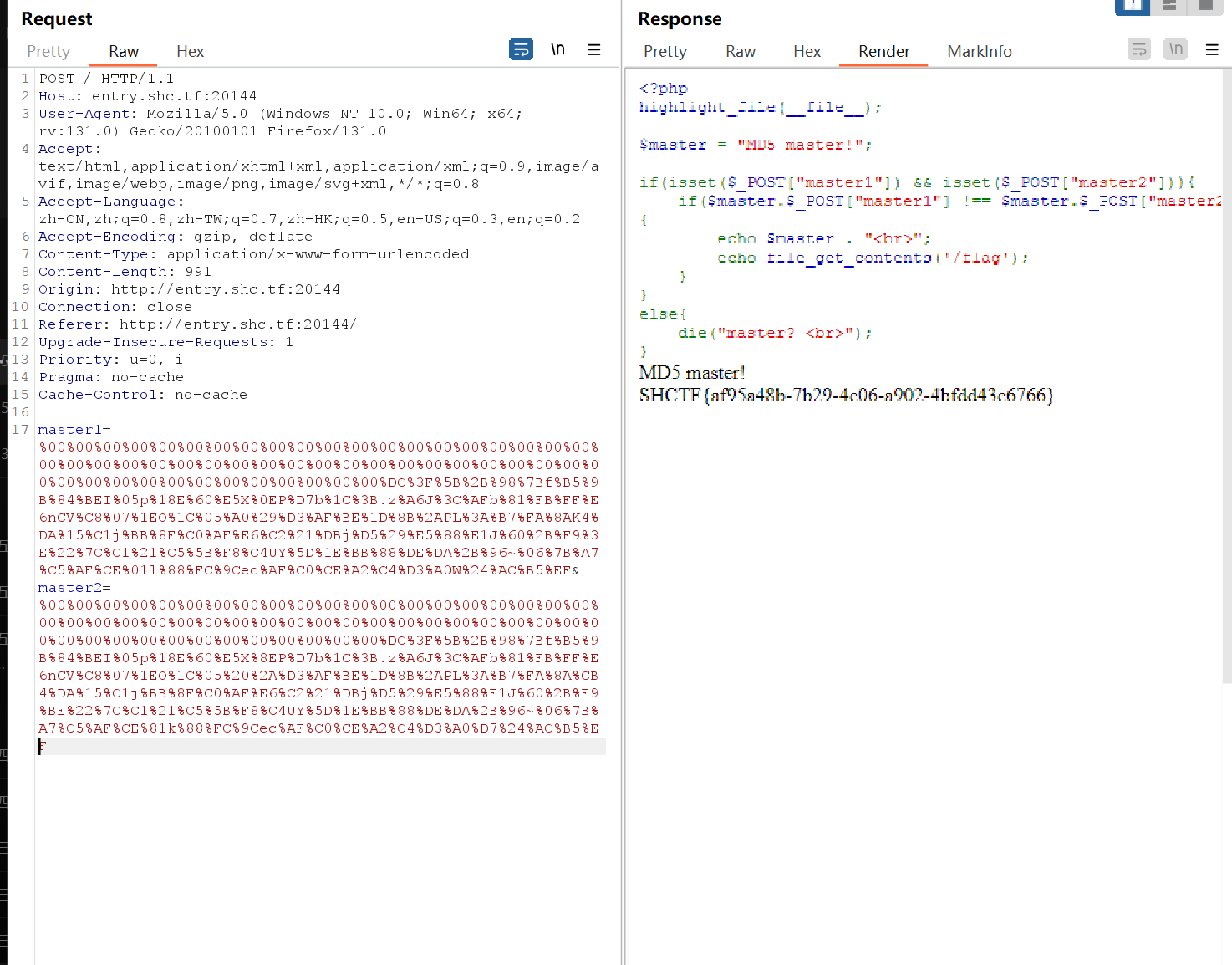
MD5 Master
1 | |
这题一开始的思路就是对的,只是由于编码的问题导致头一天没写出来,先用fastcoll对1.txt进行hash碰撞(内容是MD5 master!),然后用python进行读取内容,我php写的脚本就是一直不对,不知道为什么,然后拼接就可以得到flag了,最好用bp来发,hackbar会用url的编码问题
1 | |
Ai
小助手

Re
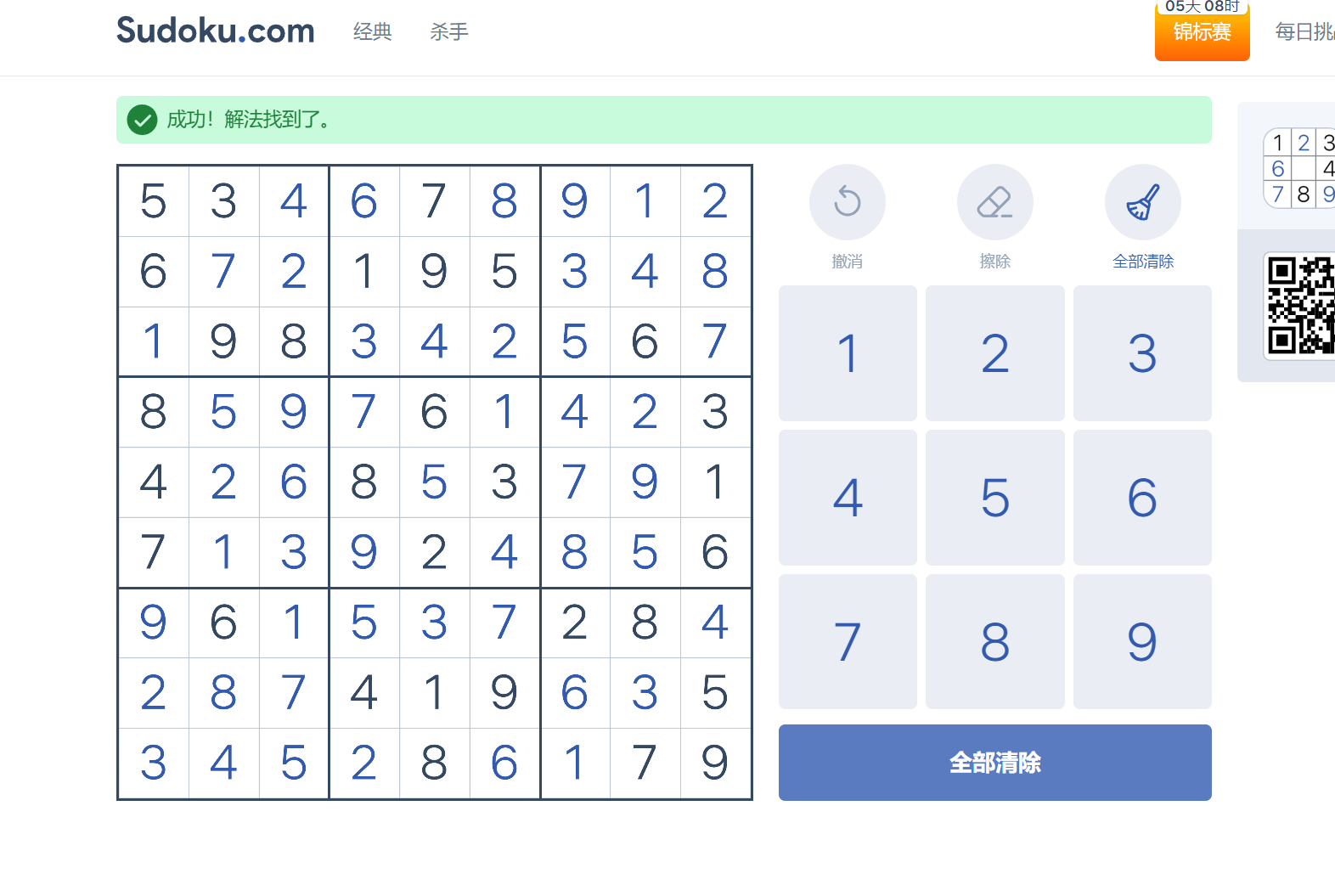
gamegame
程序简单跑一下,用ida查看一下发现flag就是数独空白下来的拼接,找个在线网站填一下数独就行
ezapk
用jeb打开定位一下,同时模拟器查看一下是什么apk
写exp
1 | |
ezrc4
看main函数和一些其他加密逻辑rc4解密,跑一下脚本
1 | |
ezxor
按逻辑进行简单的xor就行,上exp
1 | |
PPC
绑定QQ账号
在qq群绑定一下就行,然后网站出flag,记得刷新一下就行
week2
web
guess_the_number
1 | |
自助查询
前面正常的查询最后一步有提示是注释里,查询 column_comment得到flag
1 | |
入侵者禁入
考察的session,需要利用模板注入
1 | |
测试到有注入点
然后测试
1 | |
发现有flag,最后
1 | |
dickle
pickle序列化,简单的尝试了一下,注意环境需要用linux运行脚本,得到flag
1 | |
得到的flag的为类似下方的,需要简单调节拼接一下内容
1 | |
登录验证
登陆拿去cookie用jwt_tool爆破一下密钥
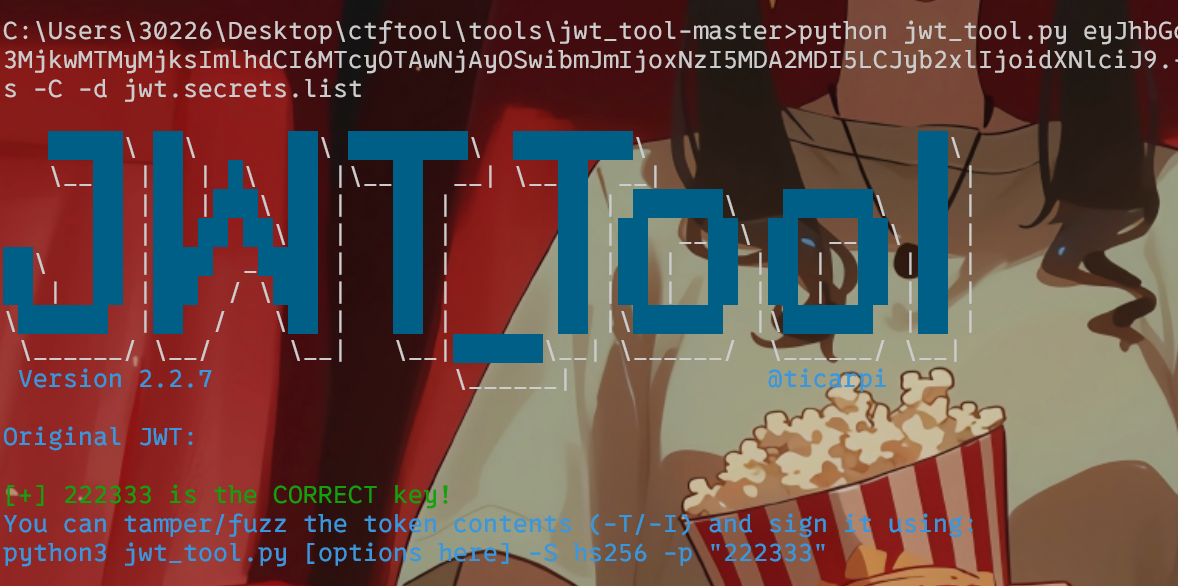
前端是弱密码admin:admin,然后也把cookie改一下得到flag
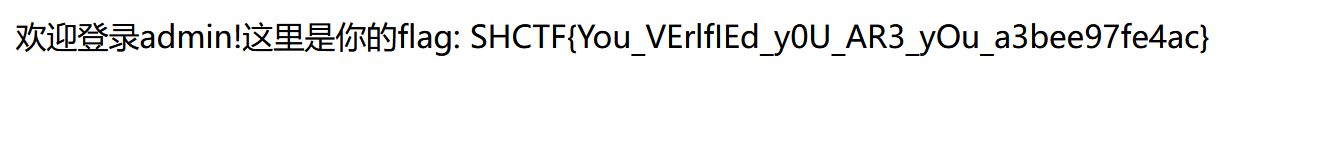
MD5 GOD!(复现)
先看源码
1 | |
题目的要求是64个用户全部签到就可以得到flag了
访问/users可以得到用户的信息
/login 路由可以登陆
/ 路由是签到的
/flag可以得到flag
定位一下关键脚本
1 | |
可以知道,只要session里的 sign 和最终 md5(salt + msg + username) 相等即可签到成功
这里的salt是未知的,但最初的账号 student 的所有信息是已知的,可以用这个账号的相关信息来做hash长度拓展攻击
hash长度拓展之前打base有个现成的脚本
接着是session伪造,SECRET_KEY 已经给出是 Th1s_is_5ecr3t_k3y可以调用flask_session_cookie_manager3.py里的代码
1 | |
自己一开始其实已经搓好脚本了,但是一直调用不好,就直接上官p了
crypto
魔鬼的步伐
1 | |
worde很大
1 | |
week3
crypto
babyLCG
1 | |
web
小小cms
先试了/admin,有登录窗口,默认密码登陆,简单搜查一下,有个数据库里面插入了flag,dump下来发现是假的flag,然后创建了一个用户试了一下前端传马看看是否执行,不行,没办法去搜了一下7.0的漏洞,直接按照这个url进行shell的https://blog.csdn.net/shelter1234567/article/details/138524342,最后上截图
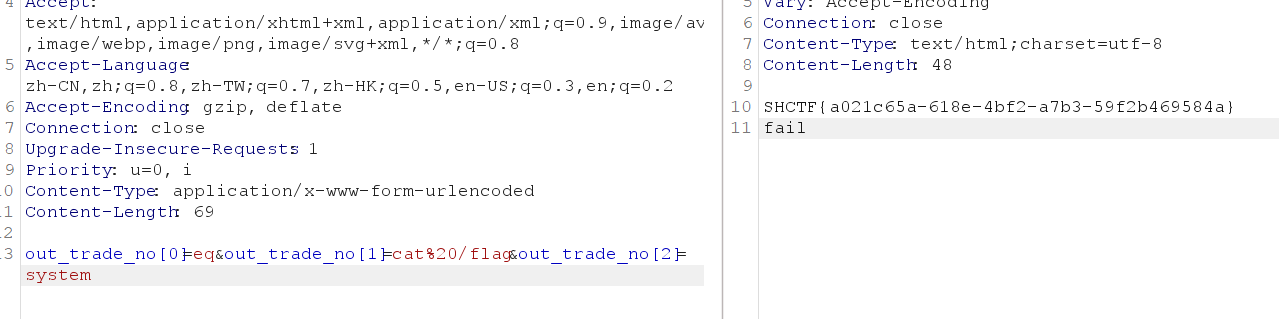
love_flask
简单的ssti的内存马,测试是没有回显的,我尝试了两种方法,一种是内部弹shell给我vps没有成功,还有一种是直接执行rce,上马
1 | |
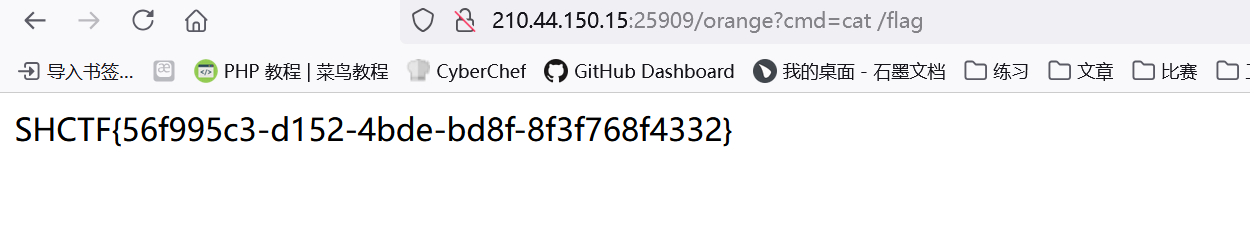
拜师之旅·番外
png的二次渲染,上脚本
1 | |
执行0=system和post发包1=cat /flag
然后ctrl+s保存图片用记事本看得到flag
hacked_website(复现)
当时扫到了www.zip,下载可以看文件,然后就没思路了当时没想到用d盾扫一下
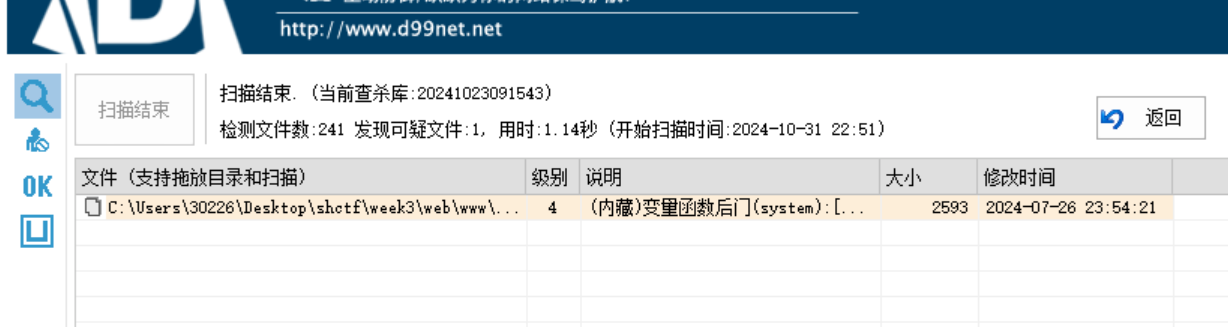
可以发现是有后面的,定位一下关键文件
文件里有这个门
1 | |
/admin里面登陆一下,fuzz一下密码
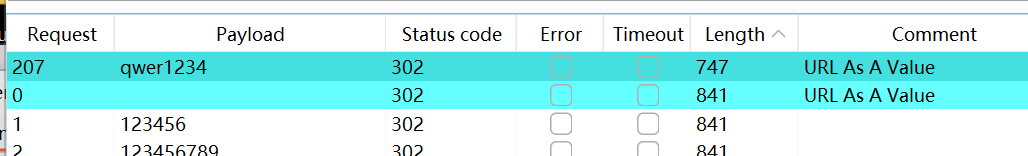
到对应的php里面输入得到flag明明挺简单的为什么没想到解法,当时全在往typecho的cve里面想
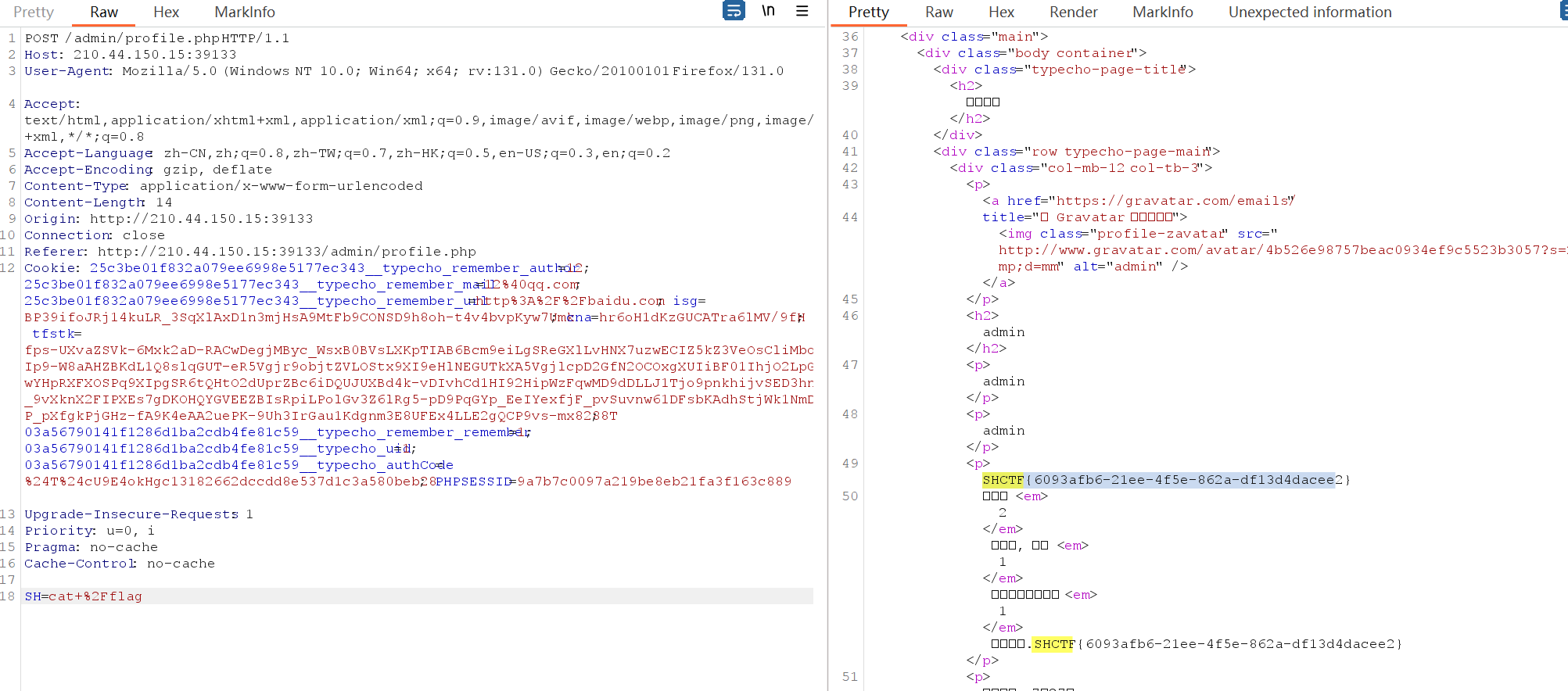
顰(复现)
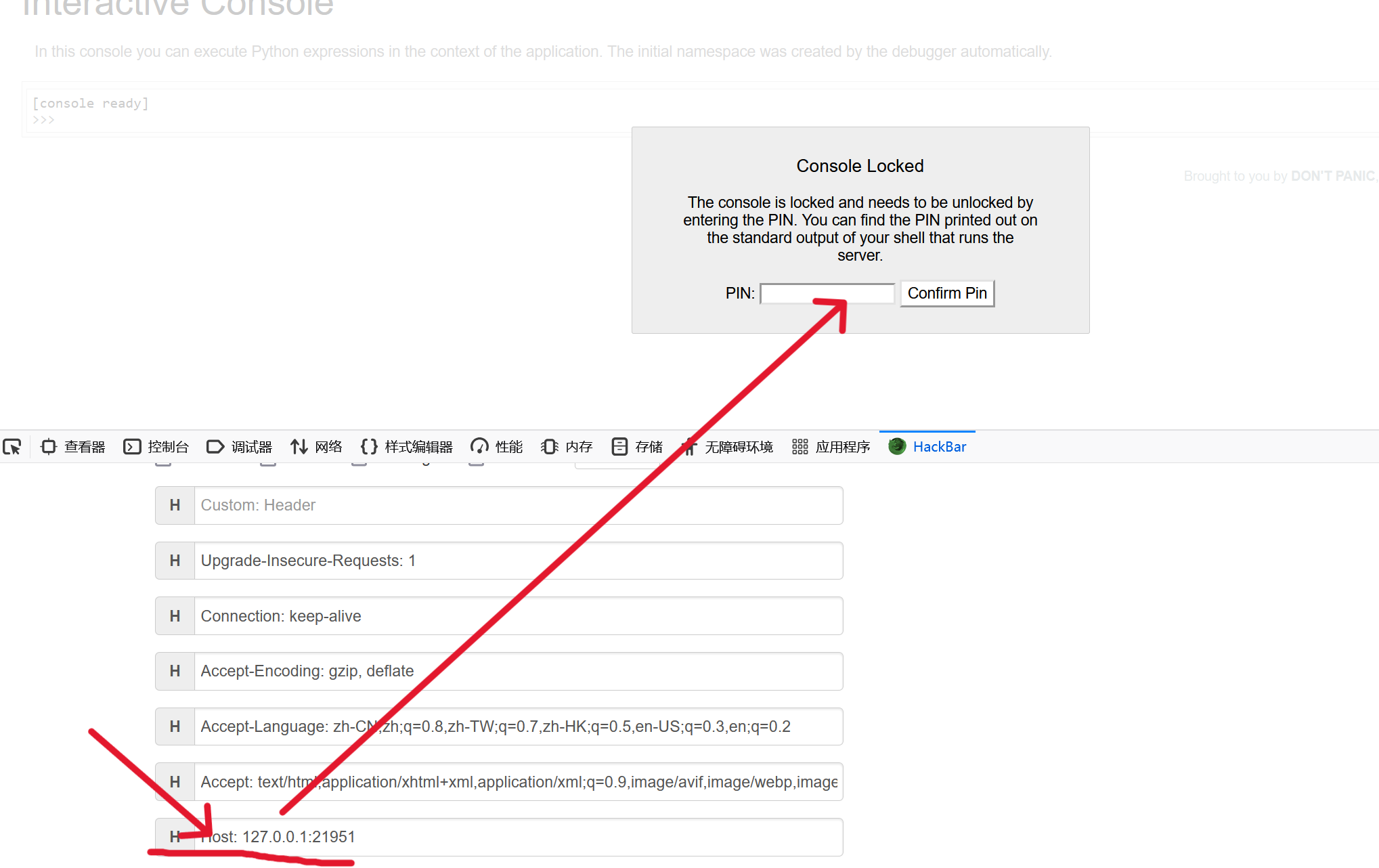
应该考察的就是算pin,写题的时候其他的数据都找到了没找到console,不明白为什么不触发orz
官p给了一个链接调试应用程序 — Werkzeug 中文文档 (3.0.x) (palletsprojects.com)
1 | |
需要host是127.0.0.1添加header Host:127.0.0.1剩余的正常都可以找到
1 | |
算pin的exp
1 | |
因为每个请求都要host,可以看源码提交
1 | |
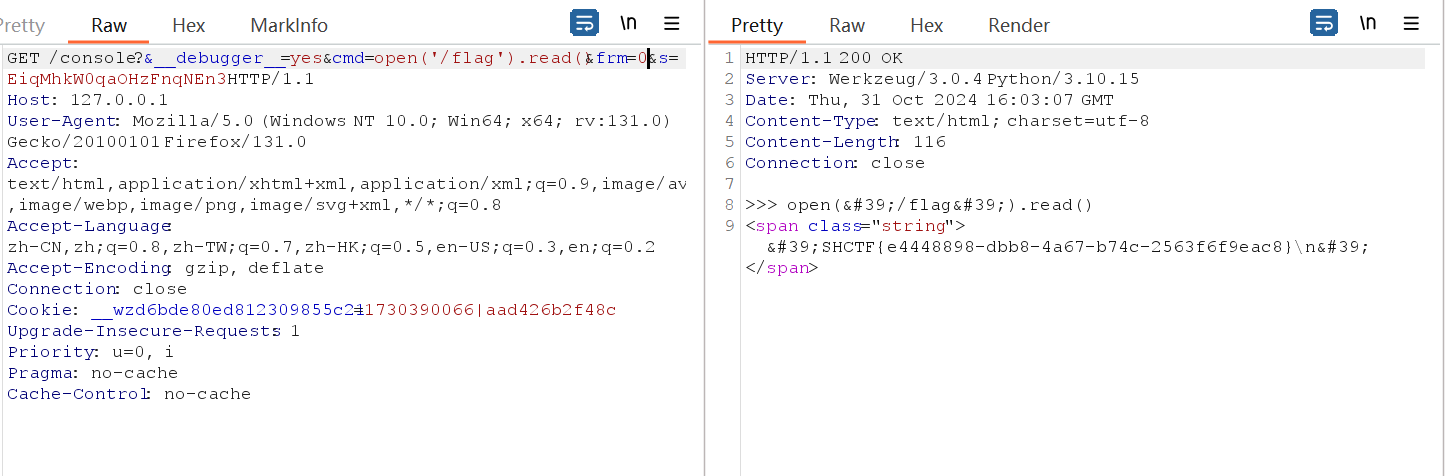
获取cookie
1 | |
week4
crypto
MT19937
1 | |
web(复现)
0进制计算器
1 | |
1 | |
这是运行通过的字符,eval可以执行的一是”=”号右侧的部分,二是cdhor()内的部分
cdhor刚好可以组成chr和ord,可以利用这两个函数来组成任意字符。chr(ord())形式的代码可以在等号右侧被转换为需要执行的代码后,再经过cdhor()执行并输出结果
1 | |
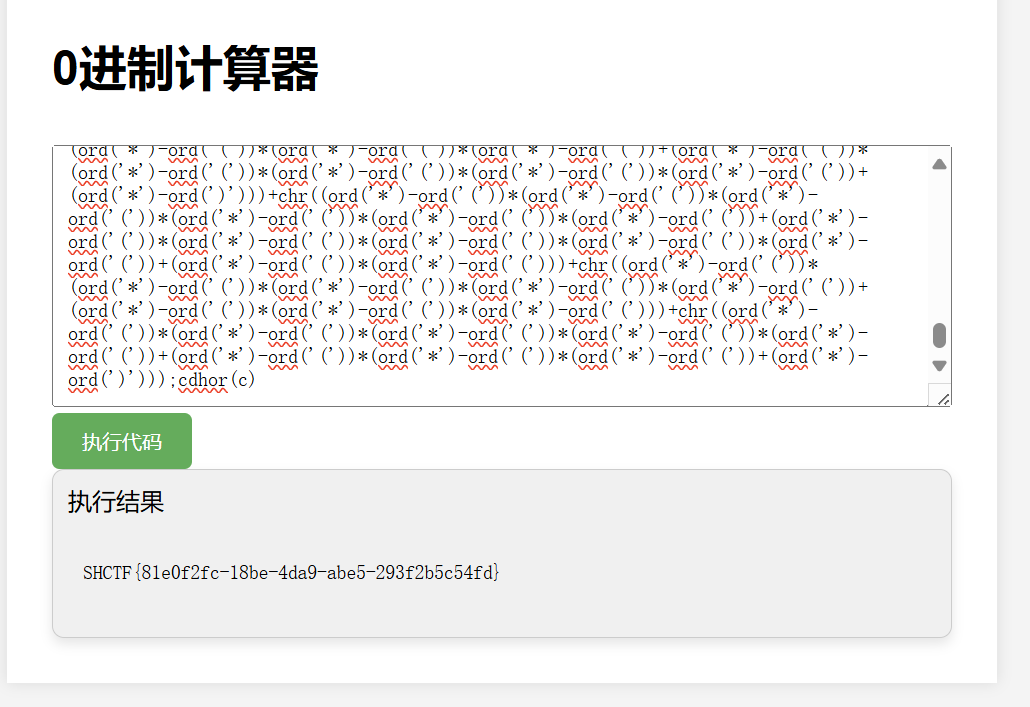
解密脚本的大致原理是设定了权值,将代码转化为ASCII再转化为二进制的形式,按照给定的权值进行转化,最后再拼接,本地可以测试测试。
0进制计算器 pro max
先上源码
1 | |
参考文章https://www.cnblogs.com/gaorenyusi/p/18242719
考察的是python栈帧沙箱逃逸(妹听过啊)
三个安全模块是通过遍历下面三个列表对代码进行过滤的,而通过栈帧逃逸,我们可以访问到全局变量,因此只需要获取到全局变量表,将下面三个列表设为空即可
1 | |
注意要把题目里的print闭合,官p说的是在前面的改
先输入
1 | |
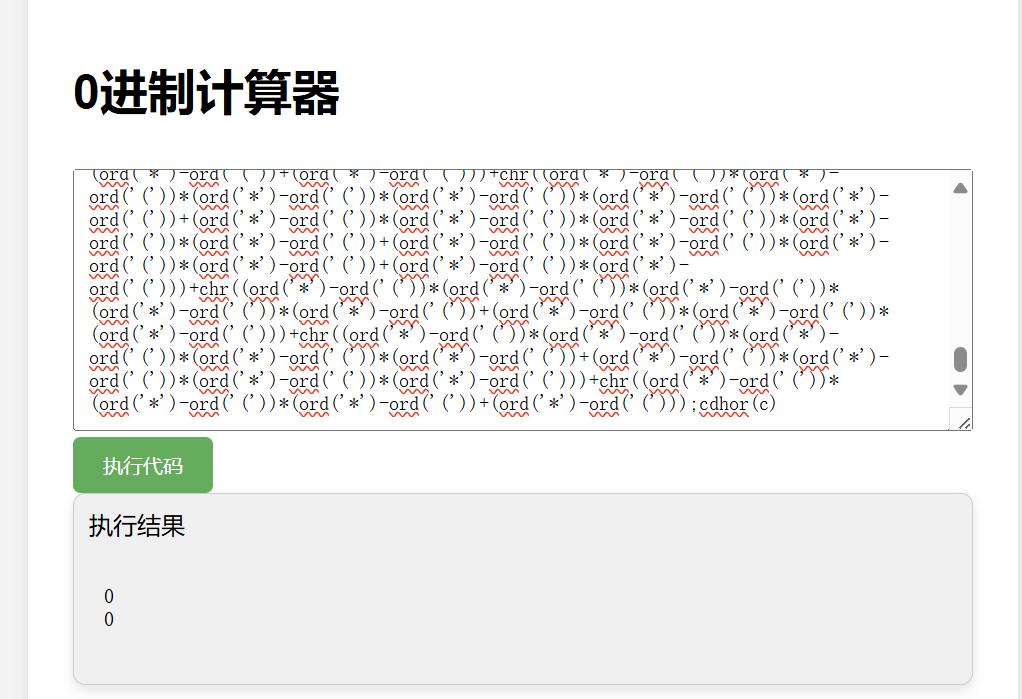
设置完成后就可以直接读取flag
1 | |
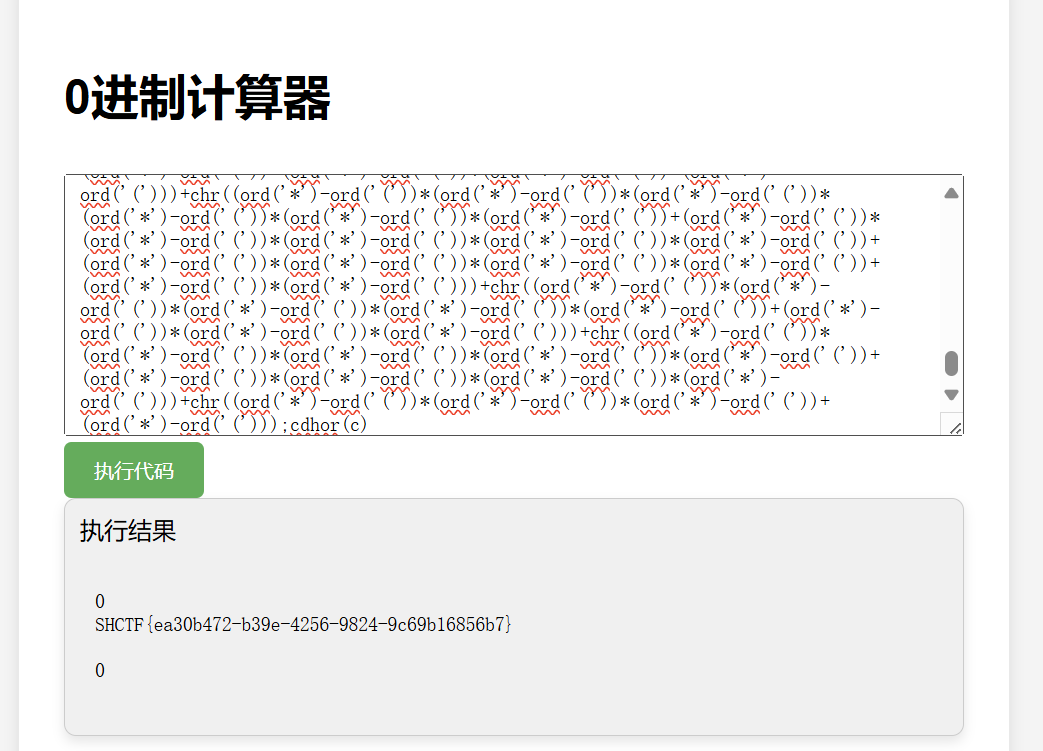
只是浮现了一下,知识点会放在学习计划中
可恶的骗子
官方给了两个解法都学习一下
0x01
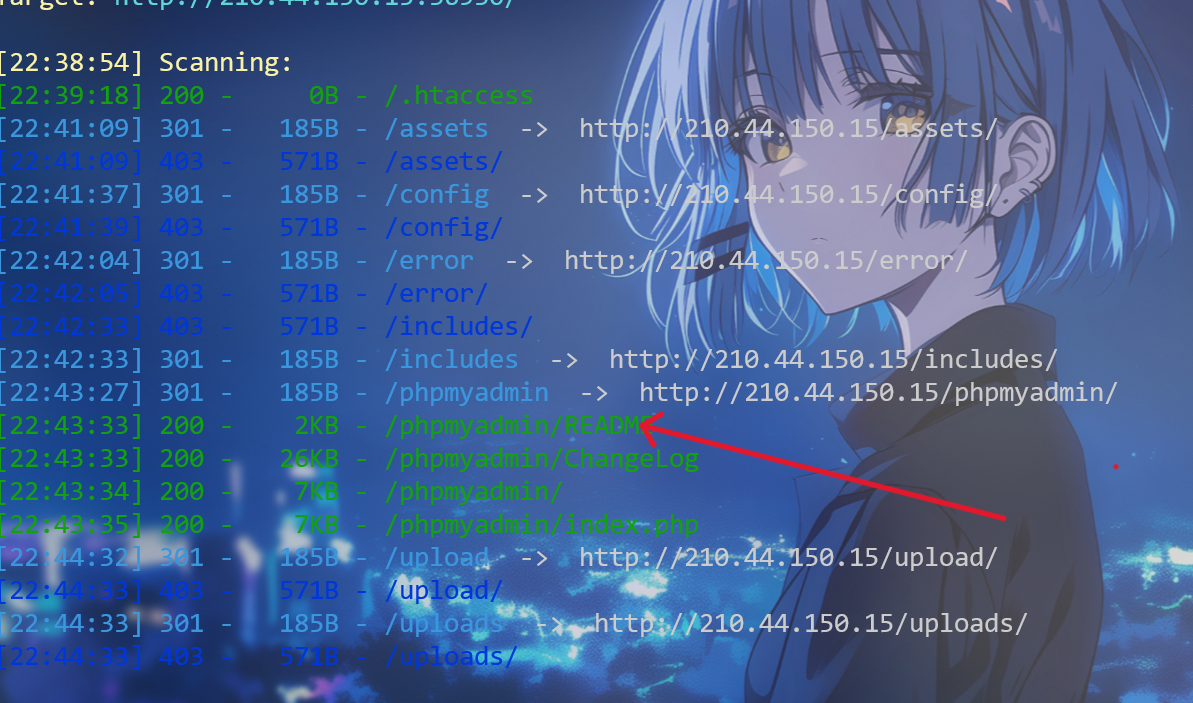
聊天记录内url拼接到靶机,显示用手机打开,使用手机ua进行访问
ClickID参数单引号报错,存在sql注入
构造一个ua头
1 | |
1 | |
加个单引号发现有sql的报错
用sqlmap跑一下看看
1 | |
最后的数据是

root::shctf_xianyu_password登入后台
具体getshell流程可以参考这篇phpMyAdmin利用日志文件GetSHELL-腾讯云开发者社区-腾讯云
登陆后使用日志写入php代码,首先启用日志
1 | |
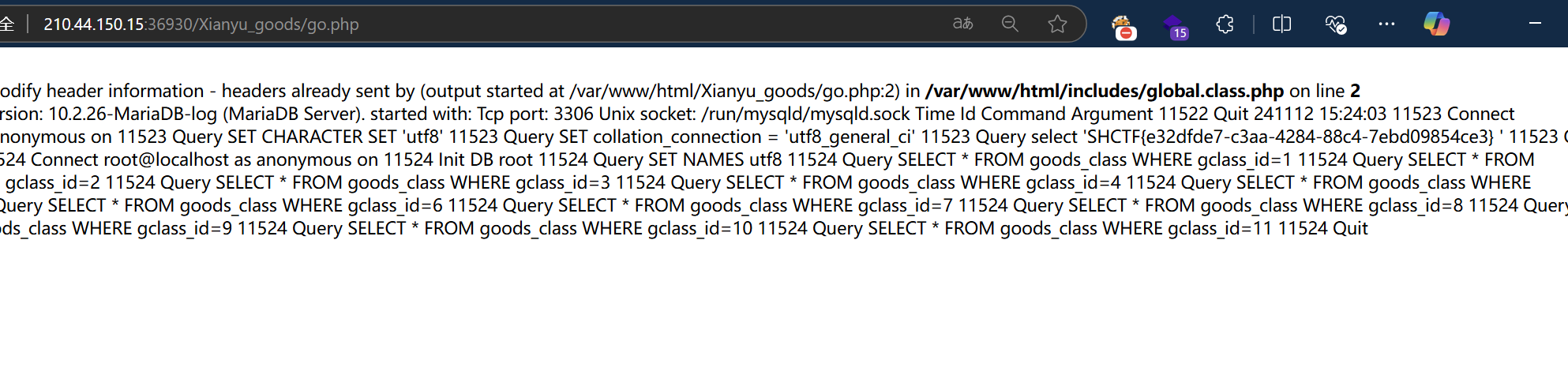
接着设置日志路径,扫描后发现Xianyu_goods下有go.php
1 | |
然后执行
1 | |
最后进入对应界面就好了
0x02
根据聊天记录,网上搜索仿咸鱼 转转 交易猫系统源码等关键字,找到此系统源码
下载后使用工具进行审计,发现index.php存在文件包含,通过HTTP参数控制
文件自己审查一下,用常用的工具审一遍。
1 | |