本文最后更新于 2024年9月21日 下午
孱弱,打是一打一个不吱声的,赛后跟着师傅复现一下
Misc png_master
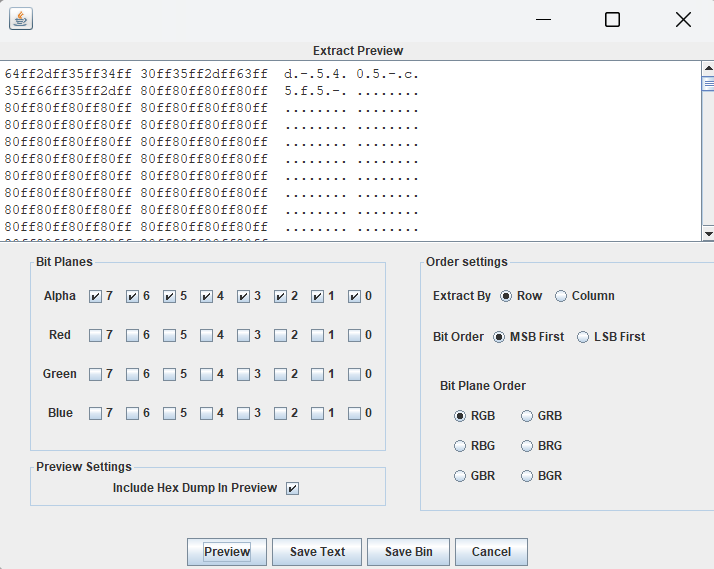
第一部分:010分析,结尾有类似base64解密的部分提取出来解密
得到第一段内容
Congratulations on finding the first paragraph of flag, but the understanding of png is just beginning.flag1:DASCTF{2fd9e9ff-e27
第二部分:
使用stegsolve来获得
flag2:d-5405-c5f5-
第三部分:
1 2 3 from PIL import Imageopen ('C:/Users/30226/Desktop/DASCTF/tempdir/MISC附件/flag.png' )'a.png' )
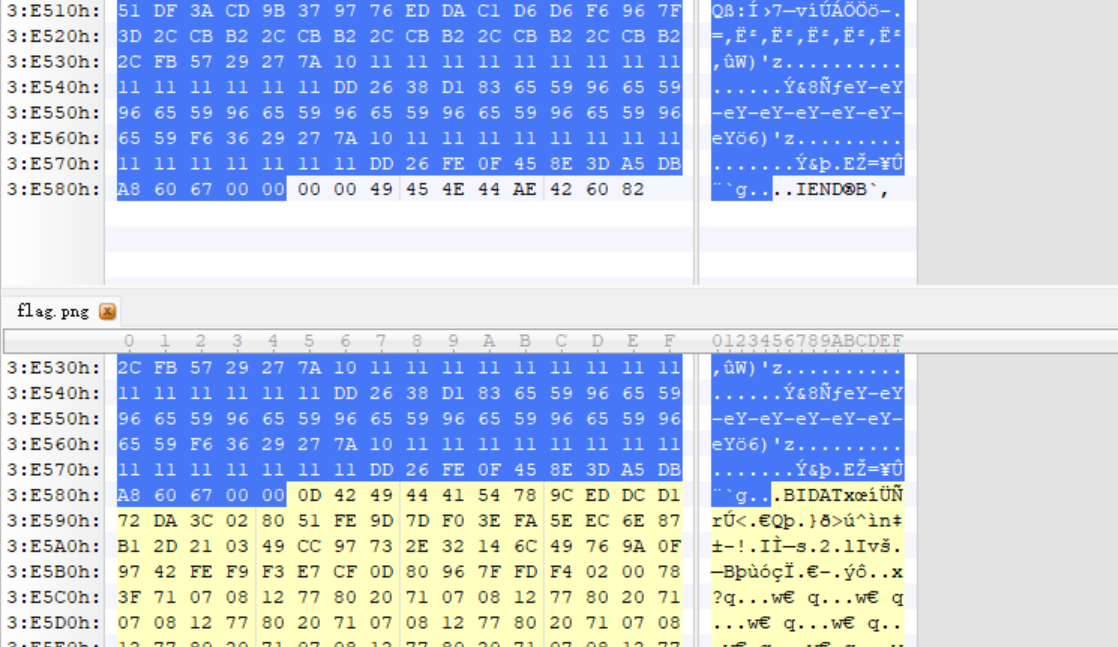
利用010进行对比发现IDAT多了一个很长的部分
把这部分单独读取出来,加上png头,得到图片
得到a19131f86216}
最后的flag是DASCTF{2fd9e9ff-e27d-5405-c5f5-a19131f86216}
EZ_zip 跟着复现一遍吧,感觉是提示点。
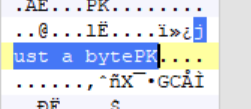
zip文件损坏的问题
使用010对两个地方进行修改,再进行解压
后面就不明白了,直接引用套神的吧
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 import pyzipperdef crack_zip (zip_file_path ):for i in range (256 ):bytes ([i])try :with pyzipper.AESZipFile(zip_file_path, 'r' ) as zip_ref:if extracted_files:return password, extracted_files[0 ]except :continue return None , None def main ():'320.zip' '' while current_zip:print (f'Cracking {current_zip} ...' )if password:hex ()else :print (f'Failed to crack {current_zip} ' )break print (f'All passwords: {all_passwords} ' )if __name__ == "__main__" :
得到密码
1 1bb99580c613a87c54e12480aa7ff8c798f71ad280f6ba69d4a4425225e4ec611bb99580c613a87c54e12480aa7ff8c798f71ad280f6ba69d4a4425225e4ec611bb99580c613a87c54e12480aa7ff8c798f71ad280f6ba69d4a4425225e4ec611bb99580c613a87c54e12480aa7ff8c798f71ad280f6ba69d4a4425225e4ec611bb99580c613a87c54e12480aa7ff8c798f71ad280f6ba69d4a4425225e4ec611bb99580c613a87c54e12480aa7ff8c798f71ad280f6ba69d4a4425225e4ec611bb99580c613a87c54e12480aa7ff8c798f71ad280f6ba69d4a4425225e4ec611bb99580c613a87c54e12480aa7ff8c798f71ad280f6ba69d4a4425225e4ec611bb99580c613a87c54e12480aa7ff8c798f71ad280f6ba69d4a4425225e4ec611bb99580c613a87c54e12480aa7ff8c798f71ad280f6ba69d4a4425225e4ec6
并且得到一个AES-ECB.txt
明显观察到这个密码是重复的11bb99580c613a87c54e12480aa7ff8c798f71ad280f6ba69d4a4425225e4ec6
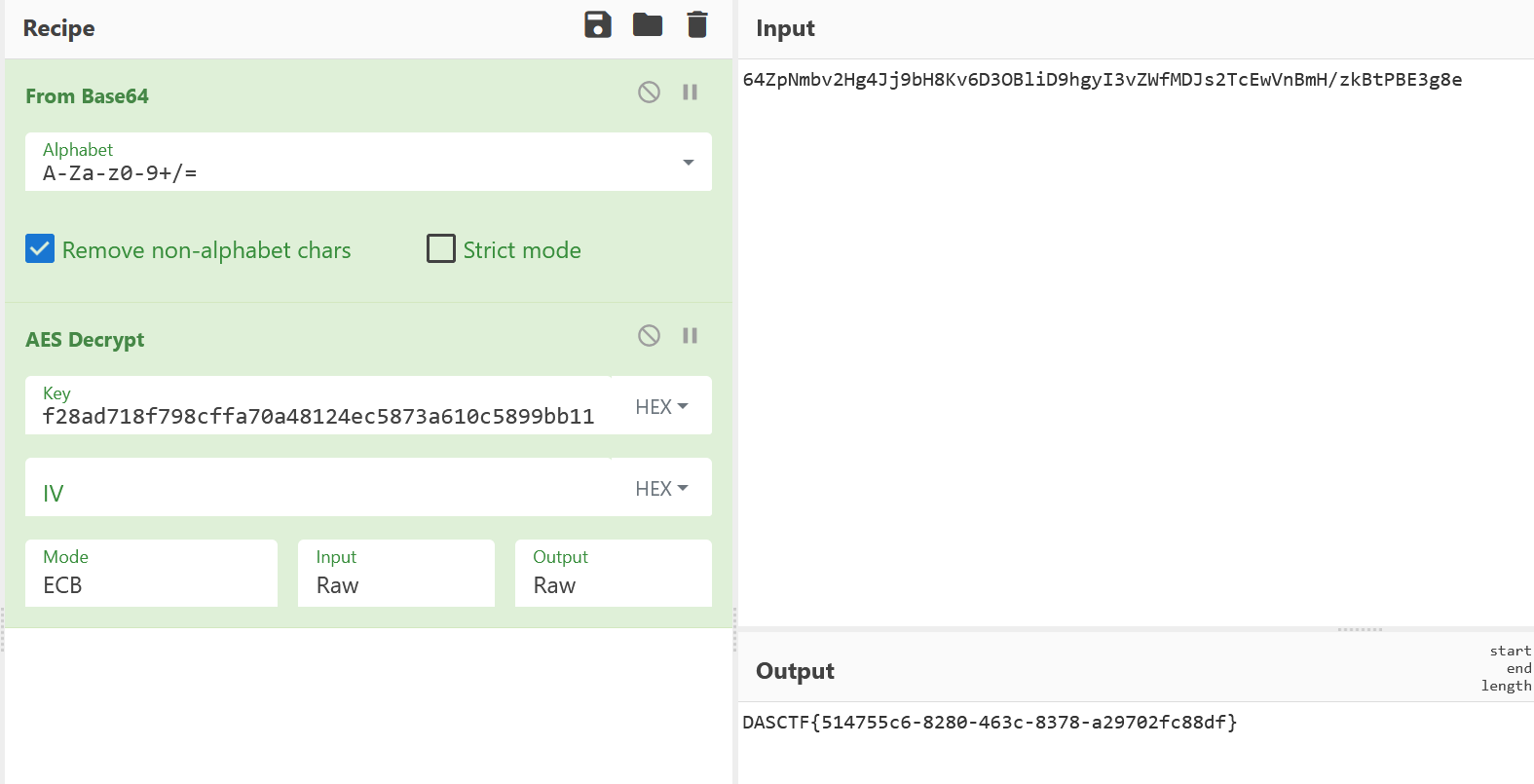
然后得到AES的内容是64ZpNmbv2Hg4Jj9bH8Kv6D3OBliD9hgyI3vZWfMDJs2TcEwVnBmH/zkBtPBE3g8e the key may be on your journey?
尝试用这个密码当aes的密码不对,猜测是解压顺序是从320–>1,而密码顺序是1–>320,因此需要反过来
1 c64e5e2225444a9da66b0f28ad718f798cffa70a48124ec5873a610c5899bb11
DASCTF{514755c6-8280-463c-8378-a29702fc88df}
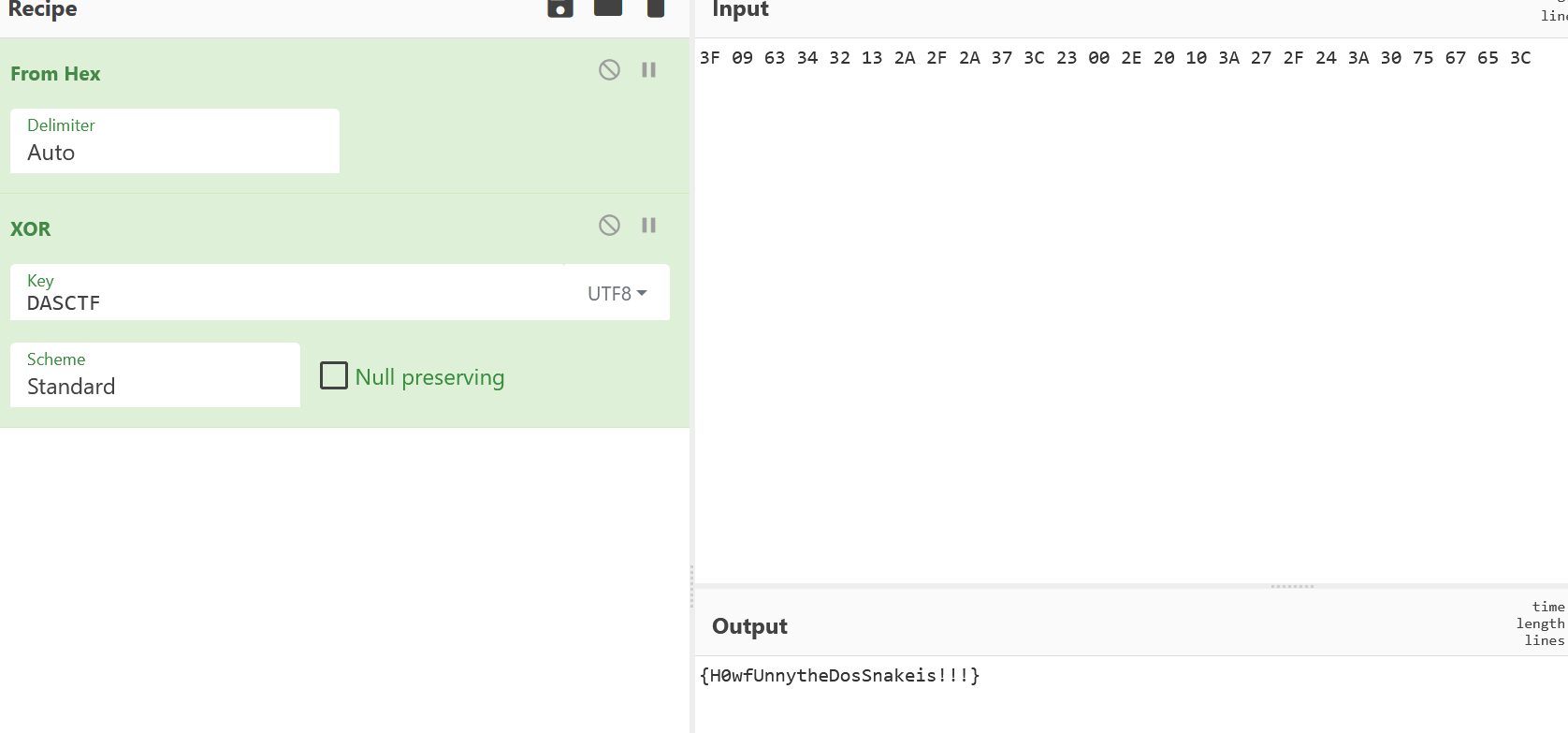
Re DosSnake ida打开,定位到dasctf
这段部分的内容与dasctf进行xor得到flag
Crypto complex_enc 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 from Crypto.Util.number import long_to_bytesdef decrypt (cipher, key ):0 ] * len (key) for i in range (len (key) - 1 , -1 , -1 ):if cipher >= key[i]:1 return decrypted_bitsdef bits_to_bytes (bits ):bytearray ()for i in range (0 , len (bits), 8 ):0 for bit in bits[i:i+8 ]:1 ) | bitreturn bytes (byte_array)int (input ("请输入密文 (c): " ))input ("请输入密钥 (key): " )eval (key_input)print ("Decrypted bytes (hex):" , decrypted_bytes.hex ())try :'utf-8' )print ("Decrypted flag (decoded):" , flag)except UnicodeDecodeError:print ("Decrypted flag contains non-UTF-8 bytes." )
背包密码